Synology integration is an option that allows the automatic synchronization of data between Tsukaeru FileBako cloud storage and a NAS (Network-attached storage) device once every five minute. This combination makes it possible to create a data management system that protects your data, whether stored online or on hardware.
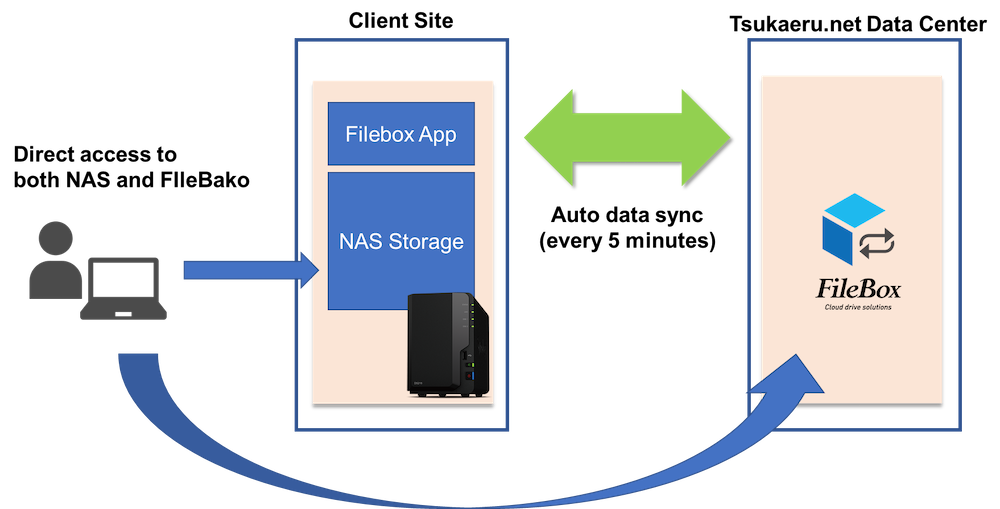
The demand for online file sharing is increasing as remote work becomes the new normal around the globe. Tsukaeru’s FileBako, a cloud-based, virtual drive service that allows users to upload data to and share it with an unlimited number of users, has been adopted by many companies due to its excellent cost performance and security. We have now developed a new synchronization option called Synology integration, designed to make Tsukaeru’s FileBako service even more convenient and secure to use. In this article, we will provide a detailed explanation of its background, new feature overviews, and setup process.
Tsukaeru FileBako is an amazing service that allows users to upload documents, images, videos, and other data to a cloud-based virtual drive. In addition, there is no limit to the number of users who can use the system to share data, and it can be used with various operating systems. Its low price also makes implementation easy and affordable for small- and medium-sized businesses.
Tsukaeru FileBako main features
・Unlimited number of users and unlimited use of 1TB
Additional capacity is available as a paid option
・Saves computer space
Download only the data you need to save space on your local device
・AD (Active directory) integration
Centralized ID/password control and remote management (paid option)
・Can be used with Windows Explorer and Mac Finder
・Available as a browser version and mobile app, allowing easy data sharing in the field or on the road
・Mail gateway function
Automatically uploads scanned data from multifunction devices, such as a scanner, to FileBako (paid option)
・Reliable security measures
AES 256-bit encryption, the world’s most secure encryption algorithm, two-factor authentication, and SSL for the web management screen ensure security
・Fast and reliable customer support
Support is available 24 hours a day by phone, email, chat, etc. in case of emergencies such as server downtime

What is NAS?
NAS stands for “Network-attached storage” and is an external data storage device that is specialized for use over a network. Compared to regular file servers, it offers lower installation costs and does not require personnel for management and maintenance. Synology Inc., which Tsukaeru has partnered with through the KSG Corporation, is a Taiwanese NAS manufacturer with global operations. Its 50% share of the European and US NAS markets make it a trusted and popular brand.
What is the new Synology integration option?
Development background
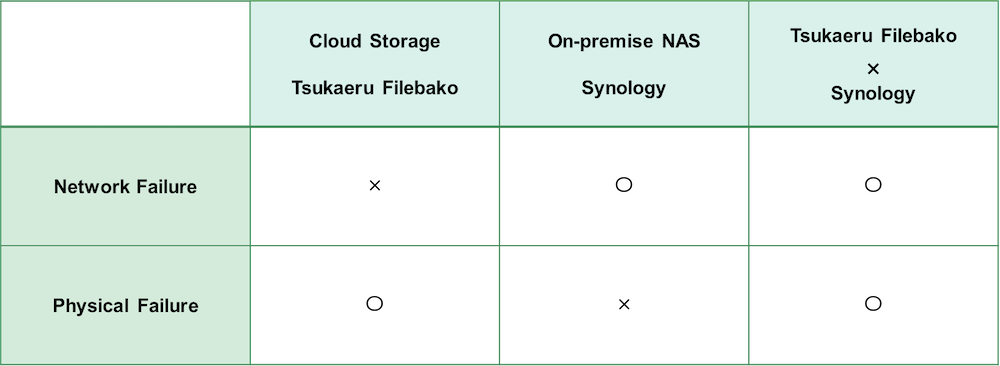
Both the Tsukaeru FileBako cloud service and Synology’s NAS are both popular choices, but each has their weaknesses, such as possible network failure with the former and downtime due to physical failures, disasters, or restoring backups with the latter. To provide even more peace of mind, we have jointly developed Synology integration, a new option that became available as of July 15, 2021.
.jpg)
Easy setup
1. [Customer side] Tsukaeru FileBako account creation
2. [Tsukaeru, KSG] NAS device setup and delivery
3. [Customer side] NAS device activation (after delivery)
NAS ancillary services
・KSG Corporation will ship the NAS device pre-set for use with Tsukaeru FileBako
・Hardware maintenance (9:00-17:00 weekdays, on-site the next business day for five years)
・Remote recovery option (9:00-17:00 weekdays for five years)
Summary
The Synology integration option synchronizes data between cloud storage and the NAS device in the on-premise environment every five minutes, creating a solid, safe, and secure system.
Tsukaeru FileBako’s new option keeps your data safe at all times
Tsukaeru Filebako and Synology integration together create an extremely convenient and secure combination. However, the only way to truly understand how it can meet your needs is to experience it for yourself.
With that in mind, we are happy to offer a free, 14-day trial period for Tsukaeru FileBako so you can see how it works.
*Synology integration is an option. To learn more, please contact one of our representatives for more details or to set up an online meeting to discuss it in person.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
In our current digital age, most of our data is now stored on computers, allowing us to easily access our files from basically anywhere at any time. It also frees us from the need to print and carry paper versions of the information. Gone is the worry about losing or forgetting important documents on the way to that important meeting.
However, just because the materials have been digitized does not mean they are 100% safe! Just as there are specific problems with paper documents, digital files have problems that are unique to that medium. One of those problems is data failure, and when it occurs, you can lose access to valuable information, or even worse, your data can be completely lost.
So what exactly is data failure and how can you prevent it from happening?
Data failure classifications and causes
Data failures can be categorized into two main types: physical failures and logical failures, each with a different cause.
Physical failure
Physical failure occurs when the parts of the hard disk are physically damaged and will not boot properly. This may happen if a hard disk is dropped or damaged by a natural disaster (ie., flooding). It can also occur if the physical parts wear out and fail during normal use.
When a physical failure occurs, you may hear the hard disk make strange noises, such as a "ticking" or "knocking" sound. It may also ask to be formatted during operation, freeze up, or reboot frequently.
A strange noise could indicate that you have a "magnetic head failure," sometimes called a “head crash.” This is the part of the hard disk that reads and writes to the data recording surface called a platter, and if this condition continues, the platter will be scratched, causing severe physical damage, which may make data recovery impossible.
Another possible physical failure is "firmware failure." For example, an electrical event may cause damage to the hard drive’s logic board, causing problems with firmware, the software that controls the device. This could result in data reading and writing being impaired. However, a firmware failure may be difficult to distinguish from the logical failure described below.
Logical failure
A logical failure is a situation where the hard disk itself is not physically damaged, but the data and folder structure stored inside is faulty. Signs that a logical failure has occurred can be files and folders that cannot be opened, file names that are rewritten without permission, or the appearance of a blue screen.
One of the causes of logical failure is mishandling or human error which causes data to be accidentally or maliciously erased, initialized, or formatted. Another cause is "file system failure," where the file system, which can be described as a file organizer, is damaged when the user forcibly terminates the system while in the act of writing data. The data itself may not be damaged, but it may suddenly become inaccessible.
.jpg)
What to do in the event of data failure
Although some of the symptoms of data failure are described above, without expert knowledge, it is not easy to determine whether it is a physical or logical failure. The more important thing is to identify the cause and take appropriate measures to prevent the symptoms from worsening and making data recovery impossible. To that end, it is highly recommended to follow these three following suggestions.
(1)Do not keep the power on
When a hard disk is experiencing a physical failure, the magnetic head will also continue to move while energized, further damaging the platter. Turning the power off immediately could stop your data from being completely destroyed.
(2)Do not keep turning the power on and off
Repeatedly switching the power on and off to check the operating status or reset the device may lead to further scratches on the platters or data loss as in (1) above.
(3)Do not disassemble
While you may want to disassemble the hard disk in an attempt to determine the cause, the inner mechanism is very delicate and any dust and dirt that may get in could worsen the failure. Also, disassembling the hard disk by yourself may void the warranty and any recourse from the manufacturer.
How can you reduce the chance of data failure?
Preventing physical failure
Due to the nature of physical failures, unfortunately, there are only a limited number of prevention measures that can be implemented. Hard disks are basically considered to be a consumable item with a limited life span. If used for a long time, it is inevitable that some kind of problem will occur. However, it is possible to reduce the chance of occurance to some extent by careful handling of the device or computer and replacing the technology every few years. In the industry, the lifespan of a hard disk is generally said to be three to five years, and it goes without saying that regular backups are necessary considering the impossibility of predicting when a physical failure will occur.
Preventing logical failure
On the other hand, there are several effective measures that can be taken to prevent logical failures, such as access rights management and virus infection prevention.
.jpg)
Access Rights Management
As mentioned above, human error or mishandling is a surprisingly common cause of logical failures. The risk can be significantly reduced by setting and managing the access permissions for each system’s functions and data. It is vital to always determine who actually needs a function or file and reconfirm/review the access permissions.
Virus infection protection
Anti-virus is not only about preventing logical failures; it is the foundation of information security. It is important to be able to update software and check for viruses on a regular basis with no hassle. Taking care of your security is directly related to protecting your important data.
Regular cloud backups provide assurance and peace of mind
While working to prevent data failures, it is equally important to take measures to minimize potential damage to your business in case of a data failure. The safest and easiest way to do this is to have backups, especially ones that use cloud services. With a cloud backup of all your files, you can minimize the fallout of a data failure by restoring from your backups.
Full management functions and ransomware protection with Tsukaeru Cloud Backup
With your computer and data backed up to the cloud on a regular basis, you never have to panic if a data failure suddenly occurs. Even if it is caused by a virus, malware, or a ransomware attack, your backup files are not affected at all, allowing you to keep your business up and running.
To learn more about the popular Tsukaeru Cloud Backup service from Tsukaeru.net and how it can help you safely and easily protect your data, please visit our website.
Click here for more information on Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
It is difficult to overstate the importance of backing up your computer or smartphone. All your data, your files, your contacts, your photos, etc. are a vital part of your digital life. This is especially true in the business world where this accumulated data is a valuable asset, making backups a must.
However, when it comes to backups, there are those who say, "It takes too long for the backup to finish, and it's a pain…" Indeed, if you have a massive number of files on your computer, it can take a considerable amount of time, sometimes as much as half a day.
In this article, we will take a look at using the cloud to backup your data and ways to make that process easier and faster.
Cloud backup in Japan
According to a survey conducted by the Japanese Ministry of Internal Affairs and Communications (MIC) in 2020, the percentage of companies using cloud services has been increasing year by year. That year it reached 68.7% breaking down to 39.4% for "company-wide use" and 29.3% for "use in some offices or departments." Data backup accounted for 36.5% of cloud service usage, a further increase from 31.4% in 2019.
Cloud backup advantages
One of the biggest advantages of cloud backup is the lower installation costs compared to large, in-house storage devices. This is especially true for small or medium-sized businesses that do not have large budgets. In addition to the cost, cloud backup does not require an in-house professional staff to perform daily maintenance.
Even if a great deal of money and manpower is used to set up your own backup, this does not necessarily guarantee efficiency and reliability. Technology is constantly changing, and it can be a struggle to stay up to date and secure from new threats. With cloud backup, on the other hand, you can rely on a professional company to monitor and maintain the latest backup infrastructure for you, thus ensuring high reliability and efficiency.
In addition, cloud backup is easily scalable. One major appeal is that you can choose the data capacity according to the scale of your business and then increase it as needed.
Cloud backup disadvantages
One disadvantage of cloud backup is that everything happens through the Internet, which can result in bandwidth problems during busy times. One solution is to set the backup schedule outside of business hours. For example, with Tsukaeru Cloud Backup provided by Tsukaeru.net, you can set the bandwidth to better manage speeds. However, no matter when you schedule the backup, as long as it is dependent on an Internet connection and depending on the amount of data, it may take some time to backup and restore.
Different backup types and how to increase data transfer speeds
What can you do if your backups are slow and time-consuming? Here are some tips to improve backup speeds that you can implement immediately.
External HDD backup
One of the most common backup methods is to save everything to an external hard drive (HDD). In this case, there are two main ways to improve the speed.
The first option is to use a USB 3.0 compatible cable for the data transfer. USB 3.0 is a new USB standard that improves transfer speeds up to three times more than the conventional USB 2.0. However, this method requires that the computer, cable, and external HDD are all USB 3.0. compatible.
The second option is to use specialized file transfer software (not the default function of the operating system) that can increase speeds and reduce backup times even for older computers that do not support USB 3.0.
.jpg)
Things to consider when choosing a cloud backup service
Due to the current global situation, more and more companies are turning to cloud backup. However, backup speeds depend largely on the cloud service used, making it very important to choose the right service. In order to choose a service with the best backup speeds based on your needs, we recommend that you compare the following points:
Cloud backup method
There are three main methods to protect your data using the cloud: full backup, differential backup, and incremental backup. Each of them will be explained in the next section below.
Server Location
Uploading time can vary depending on how far or close the server is to you and your data. Even though your information is digital, it still has to be transferred to a data center that physically exists. Therefore, backups with a cloud service using Japan-based servers will be faster for clients in the same country as compared to services with overseas servers.
Data recovery restrictions
Even if your cloud backup is fast, it is of little use if it requires a long time to restore your data. Some services enforce a certain limit on the download capacity or speed when restoring data, so make sure to fully understand any limitations when considering your options.
Cloud backup types (full, incremental, differential)
There are several cloud backup types to choose from, and with Tsukaeru Cloud Backup, you can select the most suitable format according to your needs.
With our default settings, the initial backup is a full backup with the second and subsequent backups being incremental backups. However, you can change the settings to "Always full," "Always incremental," or "Always differential."
Full backup
.jpg)
Just as it sounds, this is a complete backup of all the files on your computer. The first time you create a backup with Tsukaeru Cloud Backup, it will be a "full backup" and therefore will take the longest time.
Incremental backup
.jpg)
By default, Tsukaeru.net creates an incremental backup for the second and subsequent backups. This method detects and backs up only those files that have changed or have been newly created since the last backup, whether it was a full or incremental backup. This significantly reduces the backup time compared to a full backup.
Differential backup
.jpg)
While similar to an incremental backup, a differential backup copies all of the files, new and old, that had been added or changed since the last full backup. Because of the larger amount of data, a differential backup can take longer compared to an incremental backup.
With Tsukaeru Cloud Backup, you can also set the second and subsequent backups to be differential backups.
Tsukaeru Cloud Backup: Stress-free data protection
Backing up your data often requires time and effort, and it can quickly become an annoying chore. However, it is extremely important to protect your data on a daily basis. To ensure that this happens, it is recommended that you choose a backup method and service that is as stress-free as possible. With Tsukaeru Cloud Backup provided by Tsukaeru.net, you can easily back up your data to a dedicated server in Japan in as little as five minutes. Of course, this service provides incremental backups, which are superior in terms of speed. There are also no speed or capacity limitations when restoring. Please visit our website at the link below if you are interested in learning more about Tsukaeru Cloud Backup.
Click here for more information on Tsukaeru Cloud Backup.
(1).jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
More and more companies are considering cloud storage because of its lower implementation costs and easier data sharing as compared to maintaining and managing their own servers. However, security is still the biggest worry. If this concern is not addressed, companies are unlikely to take the plunge with confidence.
In this article, we will examine how data security works and then take a deep dive into cloud storage safety.
Cloud (online) storage security
While the term "cloud" has become common in business, many people may still only have a vague idea of what it means. First, let's take a look at what cloud storage means, and then explore the characteristics and risks of cyber attacks.
What is Cloud Storage?
In the context of computers, smartphones, and tablet devices, storage is the built-in system and hardware for storing and managing data. External storage can be connected if the internal storage is insufficient, and it can also be used for backup and storage of previous data.
Cloud storage allows users to remotely access and use stored data and applications via the Internet. One feature is that users can purchase only as much as they need. Another is that because the cloud service provider maintains and manages the storage, users do not need extra professional staff.
Characteristics of cloud cyber attacks
Cloud storage can be low cost to install and easy to use, but are there any security concerns? Next, we will cover some of the typical cyber attacks to which the cloud is susceptible.
Man-In-The-Middle attack
A Man-in-the-middle (MITM) attack, also known as a "bucket brigade attack," involves a cyber attacker intervening between a user and a service to steal or alter the data being exchanged. Even though it is a relatively old cyber attack method, recently, there has been a surge in its use.
How can a cyber attacker steal encrypted communication content? For example, suppose that two parties are using public key cryptography for communication. A cyber attacker intercepts one party’s message with a public key and sends a message with his own public key to the other party. The recipient, thinking the message is from the first party, sends data encrypted with the attacker's public key. The attacker receives the message in the middle and decrypts the data with his own private key. The attacker can then send a message to the first party that appears to be from the second party, with both parties being unaware that their encrypted communication has been compromised.
.jpg)
Unauthorized file access and hacking
Cloud service providers store a huge amount of data, including personal details, intellectual property, and confidential business and financial information. Such data is a treasure trove for hackers, making it a tempting target for unauthorized file access and hacking.
In fact, according to the "Status of Notifications of Computer Viruses and Unauthorized Access" report released by the Information-technology Promotion Agency, Japan (IPA) in February 2021, the largest percentage of damage from unauthorized access reported in 2020 was to web servers (26.7%), followed by client PCs (13.1%). For many of us, the memories are still fresh of companies using cloud services, such as Rakuten, PayPay, Aeon, ANA, etc., that have fallen victim to unauthorized access since December 2020.
Tsukaeru FileBako data security
Let's take a look at the security measures implemented by Tsukaeru FileBako to protect cloud data from MITM attacks and unauthorized access by hackers as described above.
Completely secure communications with SSL/TLS
First of all, to protect your data from MITM attacks, all communications through Tsukaeru FileBako are based on SSL/TLS.
Technology that encrypts communications over the Internet, SSL/TLS prevents third parties from stealing or altering data. Websites protected by SSL/TLS have URLs that begin with "https" and are characterized by a key mark in the browser's address bar.
In SSL/TLS communication, an "SSL server certificate" is issued to guarantee that all communication between the server and the client is encrypted. By guaranteeing the website authenticity with a server certificate, MITM attacks mentioned above can be prevented.
.jpg)
Data encryption
According to a February 2020 McAfee survey of 1,000 companies in 11 countries, 91% of the cloud services used by companies did not encrypt the data they held. As the use of cloud services expands, so does the risk of unauthorized access, and FileBako is fully capable of encrypting data.
Data encryption on client terminals
Tsukaeru FileBako runs on client terminals, but all communication is AES encrypted to ensure security. The PC platform also uses Microsoft's encryption engine to protect files.
Data encryption on customer servers
All files are obfuscated in a renamed and expanded format so that hackers and attackers cannot find the files even if they try to break in. AES encryption is also used to encrypt data on customers’ servers, but only 256-bit keys, the highest level of encryption technology, are used to encrypt files.
Password protection
The password used to log in to Tsukaeru FileBako is hashed using a salt (a random string of characters added before the password is hashed) and saved to the system.
After login, client/server communication is conducted through APIs using tokens generated by the domain administrator, and no user names or passwords are used in API communication.
.jpg)
Tsukaeru FileBako: Easy and efficient to use
As explained above, Tsukaeru FileBako has all the security measures to counter your cloud service concerns.
Files stored in the cloud can be edited and organized in a familiar way, and unlimited files and folders can be shared with other users using web links. Also, there are flexible storage options depending on the amount of data needed.
Unlimited users are available from 9,800 JPY/month (10,780 JPY/month including tax), and a 14-day free trial is available to experience how easy it is to use.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
Small and medium-sized businesses around the world are suffering from a chronic shortage of workers, and in reaction, many businesses are implementing IT solutions to make up the difference. However, while this can improve productivity, it also increases cyber security risks. The more that a company relies on IT, the greater the possibility of damage or stoppage from cyber attacks. As a result, appropriate security measures are becoming even more important for small and medium-sized businesses.
Cyber security threats are on the rise
In March 2019, the Information-technology Promotion Agency, Japan (IPA), an independent administrative agency, revised its information security measures guidelines for small and medium-sized enterprises (SMEs) for the first time in more than two years. Referencing the increase of cyber security threats. IPA states that, "there are concerns that SMEs in the supply chain may be used as a foothold for targeted attacks on the companies they serve, and it is essential to take measures as soon as possible.” IPA also points out that SMEs often have less security awareness and inadequate measures compared to large companies and are therefore easier targets for attacks.
Cyber attacks: an ongoing problem
As an example of the threats that industries are facing, in 2017, the Osaka Chamber of Commerce and Industry (OCCI) surveyed SMEs with 50 or fewer employees, mainly in the construction, manufacturing, wholesale, and service industries. Out of 315 companies, 97, or nearly 30%, had been affected by cyber attacks, and among them, 22 companies, or 7% of all companies, had been infected by ransomware. In addition, a 2019 OCCI supply chain survey revealed that while the supply chain partners of one in four companies had experienced cyber-attacks, approximately 70% were unaware of their supply chain partners' cyber-attack preparedness or damage.
.jpg)
What is ransomware?
Recently, ransomware is becoming a growing problem for businesses, including SMEs. The word is created from the combination of the words “ransom” and “software,” and can also be described as “ransom malware.”
When a computer is infected with ransomware, the stored data will be encrypted or the computer itself will be disabled. It is basically impossible to access the data or computer unless cash or virtual currency is transferred to the attackers’ designated account to obtain the encryption key. When a ransomware infection occurs, not only the computer but also all data in other externally connected storage devices can be encrypted, potentially causing tremendous problems and loss for SMEs.
Cyber security vulnerabilities
Cyber attacks are usually conducted by exploiting security vulnerabilities, but what are these vulnerabilities exactly? Simply put, they are weaknesses in a program. Computer operating systems and software often contain programming and design errors and defects. Obviously, during the development process, programmers constantly check for these problems. However, some vulnerabilities do not become apparent until the software is actually released to the market.
Therefore, IT companies that provide operating systems and software will release information about the potential problems or software updates as soon as the vulnerability is identified. However, if a malicious third party creates an attack method that targets the vulnerability before the update, a company's data may be exposed to cyber attacks.
Common tactics and countermeasures
As the three main routes of ransomware infection are websites, links and attachments in emails, and USB flash drives, the following measures are recommended to protect your company’s data:
・Infection prevention measures
The first step is to be aware of the above three infection routes and implement basic precautions to protect your company's computers. Email attachments or links should not be opened carelessly, and if there is a security concern, ask the sender for confirmation or check the extension of the attached file. Extra caution should be taken with compressed file extensions (.zip, .rar, etc.). Also, USB drives should not be used casually, even in the office.
However, no matter the vigilance of each employee, it is impossible to protect your computers and systems from cyber attacks. Therefore, it is extremely important to always update your computer's OS to the latest version to reduce vulnerability. It also goes without saying that you should install virus software and keep it updated, as well.
・Damage mitigation measures in the case of infection
Even with the above precautions, a ransomware infection is still possible, and you should plan accordingly. With a good backup system, you can restore your data even if you experience an attack. If backing up to an external storage device, make sure that it is not connected to the system to avoid the spread of infection.
Security: What is the perfect backup?
A backup is the process of duplicating the data on your computer and storing it separately in case of data loss or other unexpected situations. So, what is the best way to actually backup your important data?
.jpg)
The "3-2-1" backup rule
In the backup world, it is said that in order to perfectly protect your data, you need to follow the "3-2-1 Rule.” Originally proposed in 2012 by US-CERT, a security organization run by the Cybersecurity & Infrastructure Security Agency, an operational component of the U.S. Department of Homeland Security, it was initially thought to be too time-consuming and impractical. However, as mentioned above, it is now being reevaluated as a rule to protect data from the growing frequency and sophistication of ransomware attacks in recent years.
The 3-2-1 rule refers to the following three rules:
・Create three backups
・Save backups in two different media
・Backup one copy to a remote location
Let's take a closer look at each of these rules.
Creating the backups
With only one or two backups, there is always a possibility that one or both may be lost or destroyed, as well as the original data. A third backup creates an extra layer of security.
Storing in two different media
If all of your data backups are in the same media, you could lose it all if the problem is related to the type of media. Storing it in a variety of media, such as DVD and hard disk, or tape and online, reduces the chance that one problem could wipe all your backups.
Backing up one copy to a remote location
What if your home or office catches fire? In Japan, earthquakes are relatively common, so it is possible that you could be affected by such a disaster. If all of your backups are in one place, they could be easily damaged or compromised. By keeping at least one backup in a remote location, you can be better prepared for different types of man-made and natural disasters.
Data protection with Tsukaeru Cloudbackup +
Cloud-based backup services are an excellent option that works perfectly with the 3-2-1 rule mentioned above. By storing your data in the cloud, your data will be backed up to a location separate from your physical office. It also stores your data virtually, providing a backup in a different media as compared to physical DVDs and hard drives.
We would like to introduce Tsukaeru Cloudbackup+, a cloud-based backup service from Tsukaeru.net. This innovative and reliable service is easy to set up, requires no capital investment, and backs up not only your files, but all your accounts, settings, and OS as well.
If you are considering a cloud-based backup service as part of your security measures, or if you are considering switching from your existing service, please contact us below.
Click here for more information on Tsukaeru Cloudbackup +.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
According to a white paper on information and communications (FY 2020) by the Japanese Ministry of Internal Affairs and Communications, 64.7% of companies use at least some form of cloud services, a dramatic increase from 44.5% in 2015. As this percentage is expected to continue increasing in the future, in our most recent article, we will examine the reasons that cloud computing has become an indispensable business tool, its background, and the basics of how to use it.
What is file sharing?
The fundamental concept of cloud computing, to put it simply, is file sharing. While almost everyone has read or heard the phrase before, let's reconsider what it means.
Previous Trends
File sharing, as the name implies, refers to the sharing of a file or folder between multiple users (such as other computers) for editing. Although file sharing has been used for some time in offices, it was mainly done on Windows, Mac, and other operating systems, and mainly shared within local area networks (LAN).
Future needs for cloud computing
However, as mentioned at the beginning of this article, cloud computing is becoming the primary method of sharing files, and the demand will continue to grow for the following two reasons:
1. Increasingly larger file sizes
In the past, the most common way to send a file was as an email attachment sent via LAN. However, large and larger files, such as images and videos, are shared for collaboration and can easily exceed the size limit for email attachments.
When using the cloud to share, there is no file size limit. Files can be saved on the computer in the cloud and a link sent to another person via email or chat message, allowing them to access it.
2. Increasing demand for remote work-related online collaboration
According to the Tokyo Metropolitan Government Bureau of Industrial and Labor Affairs, the April 2021 remote work implementation rate for companies in Tokyo (with 30 or more employees) was 56.6%. Remote work, which was quickly introduced in reaction to the COVID-19 pandemic, has led to a decrease in physical office-based work and an increase in online collaborative work. Accessing the company server for file sharing or exchanging files via USB memory stick or external hard drive in the office is easy when employees are in the office. However, remote work requires different solutions, and cloud storage and file sharing services are becoming essential, regardless of the device or location. Also, new ways of working, such as "Workcation," a combination of vacation and work, are becoming popular. In order to be able to work anytime and anywhere with just a laptop, the use of the cloud is absolutely essential.
.jpg)
Advantages of cloud file sharing
As discussed above, the cloud allows file sharing regardless of the file size, the number of users, or location. The most attractive feature is that it frees you from the time and space limitations of the past and provides much more flexibility. Here are some other advantages of cloud file sharing:
・Data centralization
When sharing files via email or USB flash drive, any edits or updates must be returned with the same system. With repeated changes and exchanges, it is possible to lose track of the most current files, and mistakes can occur. However, with files stored in the cloud, all users will always have access to the latest version.
・Cost and labor reduction
Preparing, building, and maintaining internal servers requires not only money but also human resources. As the amount of data increases, it will be even more expensive to add more servers. In this regard, cloud services can be implemented at a low cost and with less time and effort of in-house maintenance and inspection. In addition, if a service with unlimited users (additional capacity can be purchased anytime) is chosen, you can flexibly adjust plans as your business grows and continue using secure and safe services.
・Effective BCP and DR measures
The COVID-19 pandemic has tested the ability of companies to respond to emergencies, which is especially relevant in Japan, where natural disasters are more common, it is important to always be prepared with an effective business continuity plan (BCP). If you rely on your own file server, there is always a possibility of data loss or damage to physical assets in the event of a disaster. However, a cloud service can be a much safer option especially if the data center is located in an area with a low risk of disaster.
.jpg)
Disadvantages of cloud file sharing
While there are many advantages to cloud file sharing, there are some issues to consider:
・Security concerns
Security is a common worry in regards to cloud file sharing. With company LANs, networks are built with a limited range and access. However, with cloud computing and its connection to the Internet, there is a small possibility that data and systems could be compromised. In this regard, cloud service providers implement various security measures including encryption or strong authorization systems. It’s important to compare the options and choose a service with stronger security measures.
・Limited customization
By building and maintaining your own servers, it is possible to design and customize them in detail, and if a problem occurs, your in-house staff can immediately investigate and respond appropriately. However, with cloud computing service providers and their scope of service, detailed responses and complete customization to meet the specific needs and circumstances of clients may not be available.
Tsukaeru FileBako: easy and efficient!
Tsukaeru FileBako maximizes the advantages of cloud file sharing while minimizing the disadvantages.
With a laptop, tablet, or smartphone, you can quickly and easily start remote working with the ability to access all your files and data from any location. Everything can be edited and organized in the cloud, and unlimited files and folders can be shared with other users using web links. There are also flexible storage options depending on your needs. Tsukaeru provides excellent security measures, including two-factor authentication, encryption, logging, and an ISO certified data center to protect your valuable data and systems.
For unlimited users, the cost starts at 9,800 JPY (10,780 JPY including tax), and our 14-day free trial allows you to try out Tsukaeru FileBako worry free!
“First Time Contract” campaign for Tsukaeru FileBako is now in effect until June 30 (Wednesday)!
The longer the contract, the more you save – with discounts of up to 300,000 JPY or more!
For more details about the campaign, please contact us via the “Contact Us”button below.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
For a long time in Japan, a method using a password-protected zip file was widely used to send and receive files for business purposes. In this method, an encrypted zip file is sent as an email attachment and the password is sent in a second email. However, this method is now considered to be a high security risk, and file sharing via cloud storage is now becoming the norm.
However, there are many different cloud storage services, and it can be difficult to choose the right one. In this article, we’ll discuss different plans, costs, functions, and security measures of cloud storage for corporations, as well as tips on how to choose the right service for your company.
First, let’s look at three main points to consider when choosing a cloud storage service: billing type, ease of use, and security measures.
Billing type
While the ease of use of a service is important, the implementation costs are often of the highest concern for businesses. This section explains the advantages and disadvantages of common billing types for cloud storage services.
Billing based on number of users
In this type of fee structure, there is a cost for each individual user.
Advantages
・Lower costs if the number of users is small
Disadvantages
・Higher costs if the number of users is large or increases in the future
・Excess storage space for large number of users
・More complicated management
・More work required when replacing employees (changing IDs, passwords, etc.)
Billing based on storage capacity
In this type of fee structure, the cost is based on the desired storage capacity. There are usually a variety of plans available, and the ‘unlimited users’ option is a popular choice.
Advantages
・Work efficiency will increase as there is no need to restrict the number of accounts
・Unlimited accounts for employees and for external parties such as business partners
・Lower cost per user as the number of users increases
・More efficient use of storage space
・Easy account management when adding or removing users
Disadvantages
・Storage space per user decreases as the number of users increases if the storage capacity cannot be changed
・Higher cost per user than the ‘billing by user’ type of service if there is only one or a few users
.jpg)
Ease of use
Ease of use is also important when choosing a cloud storage service. If your business efficiency tools are difficult to use, you can easily end up losing business. Consider the following two questions:
Do we have to learn a new system?
Employees are more comfortable and efficient using familiar systems. If they have to learn how to operate a completely new system to use a cloud storage service, it will take time and reduce productivity. You will also have to create manuals and conduct training which will require even more time and expense.
Can we easily share files and folders?
It is extremely important to confirm that you can share data in commonly-used formats (Word, Excel, PowerPoint, etc.) and large files without any problems. Another key issue is the ability to share files with users outside your company and with a mobile device such as a smartphone.
Security measures
Security measures are probably the most important factor when choosing a cloud storage service. If they are inadequate and your data or system is compromised, you can lose the trust and confidence of your customers and business partners, all of which may lead to loss and a downturn in business performance. Here are some points you should consider when choosing a cloud storage service:
2FA
2FA stands for “Two-Factor Authentication.” The standard first step is to authenticate the user with a user identification and password. If that is confirmed, a second factor is used to further authenticate the user. In general, 2FA is based on two of the following three elements: something known only to the user (PIN, password, etc.), something possessed only by the user (cash card, smartphone, physical token, etc), or a unique characteristic of the user (face, fingerprint, etc.).
Access restrictions
From a security perspective, the stricter the access restrictions on shared folders and files, the safer you will be. However, this can cause inconvenience for users. A balance of security and convenience can be found by setting up detailed user permissions to access the shared folders/files or by restricting access by device.
Log monitoring and version control
Log monitoring allows administrators to see the account activity for each user, such as deletion, upload, and login history. You should also check to what extent file version control is available.
.jpg)
What Tsukaeru FileBako can do
Tsukaeru FileBako is a new cloud storage service that creates a new work style that allows users to connect with anyone, anywhere, anytime. Featuring an unlimited number of users, you can share, edit, and synchronize files on any device.
1. Unlimited number of users
While most other companies have one-user-one-license systems, Tsukaeru’s economical Business Plan is available starting from only 9,800 JPY (10,780 JPY with tax included) per month, regardless of the number of users. In addition, it comes with a generous 1TB capacity.
For example, with 100 users, the cost would be approximately 100 JPY per user per month. If slightly less capacity allocated per user is acceptable, for 1,000 users, the cost would only be 10 JPY per user per month. All corporate plans have no limit on the number of users and provide flexibility when dealing with sudden increases in staff at no extra cost.
2. Add, edit, and share files with a familiar system
Tsukaeru FileBako is a file server type cloud storage service. You can enjoy all the benefits of the cloud with the familiar folder structure and operation system. Adding, editing, and synchronizing files is almost the same as using Explorer on a desktop computer. With no file size limit, there is no need to deal with a common cloud storage error message: "The import file is too large to upload.”
3. Secure and easy file restoration and version control
While there are many large capacity, low cost cloud storage solutions, the security of your most important files and data should be your highest priority! With a Tsukaeru FileBako, it is easy to easily share files with external users or team members with just a few clicks. Web links for sharing can be set with passwords and expiration dates, ensuring even higher levels of security. It is also possible to create shared folders for collaborative projects and to control folder access permissions for each user.
Why choose Tsukaeru?
Tsukaeru’s cloud services have been used by customers all over Japan for more than 20 years.
1. Ideal location for cloud service data center
Because Tsukaeru’s data center is located in Nagano Prefecture in Central Japan, data can be accessed at a much faster speed than services relying on overseas data centers. In addition, Nagano Prefecture is far from the Tokyo metropolitan area and is relatively disaster resistant, making it very effective for BCP.
2. Excellent customer support
All of the Tsukaeru customer center staff are dedicated in-house operators and are available to help you solve your problems with our extensive expertise and experience. We can be reached not only by phone, but also by e-mail and chat, so you can rest assured that we will be there when you need us.
If you are interested in Tsukaeru FileBako, please feel free to contact us. We'd even be happy to set up a free trial for you!
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
To improve your company’s performance, improving business efficiency is an important step. One of the best ways to maximize that efficiency is through the smart use of IT tools.
In any industry, cloud computing is now essential, but only approximately 30% of companies use it for data backup. In this article, we’ll take a look at cloud backup, not only an effective time saver but also excellent disaster preparation.
Effective time saving tools
According to the Japanese Ministry of Internal Affairs and Communications survey on telecommunications usage trends for fiscal year 2019, 64.7% of all companies in Japan use cloud services. The most common use was for file storage and data sharing, an efficient way to save time as compared to the traditional use of paper-based files and email attachments.
While there are many tools to improve business efficiency and productivity, it is important to clearly define the purpose of their introduction. If just based on the vague concept of "saving time," the results may not be worth the effort to implement the tool.
BCP(Business Continuity Plan) and DR(Disaster Recovery)
Data backup is another reason for adopting cloud services. According to the survey mentioned above, 31.4% of all companies in Japan use cloud services for this purpose, not only to protect against human error, but also as risk management for large-scale disasters. Cloud-based backups should be part of your business continuity plan (BCP), allowing your company to continue or quickly recover its core business while minimizing damage when faced with a natural or man-made disaster.
DR (Disaster Recovery) is a similar concept to BCP, but it differs in that BCP focuses on the whole business, while DR focuses on the recovery and restoration of data and computer systems that have been affected by disasters or terrorist attacks. Think of BCP as an umbrella plan and of DR as part of that plan.
What is Disaster Recovery (DR)?
As mentioned above, disaster recovery refers to the recovery of data and systems that have been affected by a disaster, as well as the policies and procedures to be taken.
The key elements in DR are RPO (Recovery Point Objective) and RTO (Recovery Time Objective).
As briefly mentioned in a previous article on backup testing, RPO is an indicator of the maximum length of time in which data might be lost when restoring your system after a disaster. For example, if the RPO is set at 0 seconds, data loss will be avoided regardless of when the disaster occurs. However, if the RPO is set as the previous backup, all data from the most recent backup until the time of the disaster will be lost.
In contrast, RTO refers to the maximum acceptable time that your systems can be down after a disaster. For disaster recovery, the shorter the RTO, the better. For example, if the RTO is set to one hour, data and system recovery must be completed within one hour of the disaster occuring.
.jpg)
Why is DR necessary?
As more IT tools are used to improve business efficiency, so does the amount of important company information stored in the system as data. The impact of a huge data loss due to a disaster or the inability to access the system for an extended period of time can be immeasurable.
According to Infrascale's Disaster Recovery Statistics (2015), one hour of downtime can cost a small business $8,000, a medium business $74,000, and a large business $700,000. Companies without a DR plan in place may be forced to suspend business, thus lose the trust of customers and suppliers, and may be exposed to information leakage risks.
Case Study (Europe): Post-fire data restoration through DR implementation
On March 10, 2021, a fire broke out at one of OVHcloud’s four large data centers in Strasbourg, France, located along the Rhine River. As a major European cloud service company with more than 1.5 million customers worldwide, it is easy to imagine the amount of data that OVHcloud was managing.
Immediately after the fire, the company announced their recovery plan and had their servers up and running again 10 days later. Although some data was lost due to the fire, the company was able to minimize the damage due to its DR planning during normal times.
How to select the best system for DR measures
In terms of DR effectiveness and cost, there are two major types of systems for consideration.
1.Tape drive backup (cost: high, RTO: very long)
As the name implies, this is a method of backing up data on a "tape" drive. The main advantage is that it is easy to move data as it is stored on a physical medium. However, it is necessary to consider the environmental conditions for storage and the operational costs involved, such as follows:
・Room temperature and humidity must be strictly controlled, requiring a storage location with proper environmental controls outside the office.
・It can take time to access or download data.
・The complexity of such a system requires more expertise and specialized equipment than other backup methods, resulting in higher maintenance costs.
When trying to restore data stored on tapes, it is possible that data may be lost due to poor storage conditions. Also, repeated physical handling may damage tapes which can cause data loss.
Because of these concerns, backups to external disks or the cloud are becoming the mainstream as new alternatives to tape.
.jpg)
2. Remote network backup (cost: high, RTO: short)
A second method is to back up data to a different location through a network. This is effective for DR as backup data are stored in a separate location from the main data. In addition, although the restoration process still requires a restore, RTO can be kept to a shorter time compared to tape media.
However, the cost is usually higher because a separate backup location must be maintained by the company.
.jpg)
The importance of data replication
Data replication creates a backup system from the original data, allowing for an immediate switchover in the event of a failure. This can be considered as a “duplication" of the system. This backup system will continue to operate at all times, an extremely effective DR solution from the perspective of RPO.
However, this replication can be very costly if you create and maintain the system yourself; it could cost as much as operating your main system. Also, if the main data are affected by a virus, it will be replicated directly into the backup system.
Tsukaeru Cloud Backup + features and benefits (cost: low, RTO: short)
Tsukaeru Cloud Backup + automatically backs up the entire system according to the customer’s settings. As a cloud-based backup, no hardware or other equipment is required, lowering the initial and operation costs.
In general, the cost of implementing data replication as a DR solution is quite high. However, Tsukaeru Cloud Backup + minimizes the cost of maintaining duplicate systems through system replication while also reducing RTO to an incredibly short period of time.
Tsukaeru Cloud Backup +: The low-cost, labor-saving solution
Protect your data at the low cost of 30 JPY per day/0.98 JPY per 1.0 GB, depending on the capacity you need. Also, as a cloud-based backup, there is no need for specialized IT or security knowledge or complicated setting management. Furthermore, since the entire system image is backed up at once, backup time can be significantly reduced compared to normal file backup.
Cloud Backup + is available to try for free for 30 days, so please consider trying it out to see if it fits your DR needs.
Click here for more information on Tsukaeru Cloud Backup + (Plus).
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
A server can be indispensable for running a website and other applications.
hoosing the right server is crucial to ensure stable website operation. However, with so many server options, it is easy to get confused about which one to choose.
In our newest article, we will discuss what to look for when choosing a server and share tips on how to choose the right one.
What is a server?
In order to create a website and publish it on the Internet, you need a space called a "server." This is where the necessary elements and files (text, images, videos, etc.) are stored for your website.
This server can be set up by a company or an individual, but usually, you must build, maintain, and
troubleshoot the server on your own. These challenges are often why many companies take advantage of renting a server. By signing up for a service, the management of the server is the responsibility of the service provider, and there is no need to prepare your own physical server.
Points to consider before choosing a server
There are many corporate options available, and choosing the right one for your company can be a daunting task. Therefore, when choosing a server, it is important to understand your needs and other important points in advance.
Estimate website traffic
One of the first steps is to determine how many users will access your website. This will help clarify the importance you should place on the specifications needed. If the server specs and the corresponding transfer volume are not sufficient for the expected traffic volume, problems can easily occur.
Determine your needs and budget
When choosing a server service, make sure you know exactly what you are looking for to meet your needs. In this way, when examining similar options, you will be able to choose the best server based on your predetermined priorities. A clear understanding of your available budget beforehand is also important.
_2(1).jpg)
How to choose the right corporate server
Below are some tips on how to choose the best corporate server for your needs. If you are considering a new server contract or switching to a new provider, please refer to this section.
Understanding the different types of servers
There are three main types of servers for rent: shared, VPS, and dedicated. Let's take a look at the features, advantages, and disadvantages of each type.
A shared server is a service in which multiple users share a single physical server. As the cheapest option, it is very popular for those with simple needs (website operation, mail account management, etc.). On the other hand, customization can be limited, and performance may be affected by other users.
If we compare it to a house, a shared server is a "share house" with individual bedrooms but a communal kitchen, bathroom, etc. The landlord (Tsukaeru in this case) manages the common areas, while the tenants manage the inside of their own rooms. This is recommended for those who want to operate in the common areas to a set specification but do not want to spend a lot of time managing them.
Recommended: Personal websites, small websites, etc.
Advantages
・Low cost and affordable
・No technical knowledge required; easy to implement
・Service providers responsible for maintenance, etc.
Disadvantages
・Can be affected by other users
・Limited customization
・Performance can be slow
A virtual private server (VPS) is a service that uses virtualization technology to divide a single physical server to provide separate virtual servers for each user. Each virtual server has its own independent environment (individual memory, disk, software, etc.) which is hardly affected by the other virtual servers.
A VPS can be compared to an "apartment." It has high specs and flexibility, the price is reasonable, and the cost performance is excellent.
The difference between a VPS and a shared server is that the administrative rights are with the tenant who can customize by remodeling (changing OS, building applications, etc.) in the apartment. However, knowledge about the operation is required. As this is a good compromise between a shared server and a dedicated server, it is recommended for corporate users.
Advantages
・Administrator privileges, allowing detailed customization
・Can choose OS, CPU, and other specifications
・Not affected by other users
Disadvantages
・Some knowledge about servers is required
・May not be as scalable as a dedicated server
A dedicated server is a service that provides a single physical server for your use only. This option offers the highest degree of freedom and stability but at a slightly higher cost.
This type of server allows you to manage the entire physical server, creating the image of a "single-family home." High-performance, stable, highly scalable, and customizable as desired, it is also not influenced by other users. However, the cost can be rather high, and specialized knowledge is required for operation, making a dedicated server more appropriate for advanced users.
Advantages
・Ownership of a high-performance server
・Complete control of customization
・Not affected by other users
Disadvantages
・Higher price
・Required expertise
Specifications: CPU and memory capacity
Depending on the server specifications, there are differences in the speed and response for website access. In particular, you should pay attention to the central processing unit (CPU) and memory values. The higher the values for both, the better the performance. Of course, you should also pay attention to the disk space and estimate how much you will need with some margin for safety.
Network connection: check the speed and transfer rate
The strength of the network line varies between servers. If you are expecting a large amount of traffic on your website, pay attention to the network line speed when choosing a server. In addition, be aware that some servers have transfer volume limits (e.g., up to XX GB per month).
Automatic backup service: a must for business use
It is a good idea to have an automatic backup service in place just in case. With this service, if something as simple as accidentally deleting a file from your website or something even more serious occurs, you can quickly restore what you need. When renting a server for business purposes, this is basically a must-have feature.
Support: a common blind spot in choosing a server
One often overlooked issue when choosing a server is the level of customer and technical support. A high level of support provides peace of mind and confidence when problems occur or when you have questions. It is also important that there are a variety of communication channels available, such as phone, email, and chat.
What is the best corporate option?
If you are in the market to rent a server, we recommend Tsukaeru servers, which are used by many companies and organizations throughout Japan. In particular, Tsukaeru Cloud VPS is a popular service with a reputation for its reasonable price, ease of use, and excellent customer and technical support. One of the many reasons for this service’s popularity is the wide variety of plans that can be used for various purposes by individuals and corporations.
Stress-free website management with Tsukaeru Cloud VPS
Currently, Tsukaeru Cloud VPS is running a special campaign that offers up to 50% off the usage fee. In addition, with a new contract for one year or more, the initial cost will be waived. The campaign is only available until April 28, 2021, so please take this opportunity to check it out.
Click here for details about Tsukaeru Cloud VPS.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
The Internet, social media, and smartphones have all become integral parts of our lives. We can keep in touch with our friends, check the news, go shopping, etc. However, while this may make our daily lives more convenient, there are some new problems that have appeared. One of the most significant ones is "online privacy.”
Is your online privacy really safe?
As the Internet becomes more and more integrated into our society, online privacy is becoming just as important as privacy in real life.
For example, if your online shopping account password is revealed to a third party, your personal information such as credit card number and home address could be at risk. Even without a password leak, there is still a possibility that you could be identified from the photos and information you post on social media or even be a victim of online stalking.
Growing global interest in personal data privacy protection
More recently, internet users’ concerns about personal data being collected by websites and online advertisers have been on the rise worldwide. Most websites and social media sites collect data such as user demographics and website page browsing history for targeted advertising and other purposes. To guard against potential problems, there are specific actions that internet users can take.
.jpg)
Seven steps to protect your data privacy
So, what can an individual do to better protect online data privacy? Here are seven ideas to help you do just that.
1. Set a strong password
Create and use a complex password with a combination of letters and numbers at a minimum. A mix of uppercase and lowercase letters, numbers, and symbols is even more effective.
2. Don’t use the same password for multiple sites
If you use the same password for multiple sites, all of them are at risk if one is compromised. Even if you have a basic password and use only one different character for each site, this is much safer than using the exact same password. If you can't remember that many passwords, there are many free and paid password managers you can use.
3. Think before clicking "I agree"
When visiting a website for the first time or installing an app, you often see a message about the "Privacy Policy" or "Data Collection Policy," Do you usually just click "I agree" without considering what it means? While it may take more time, you would be wise to take a look at the policies of that site or app. Increasing your awareness of online privacy on a regular basis will help you protect your personal information.
4. Review your privacy settings
Recently, many social media and search services have begun to offer detailed "Privacy Settings" management screens. It is highly recommended that you check and review the privacy settings and details for each and every item.
.jpg)
5. Review your social networking use
Do you usually casually post information about yourself, your neighborhood, your children, etc. on social media? Although major social networking sites such as Facebook and Instagram have taken measures such as automatically removing location information from posted photos, it is still possible to discover personal information from what you post. You should always keep in mind that people other than your friends and followers may see your posts and be cautious when posting.
6. Use two-factor authentication
More and more services are offering a two-factor authentication option that combines not only password entry but also email, SMS, or app authentication. With two-factor authentication enabled, even if your password is compromised for some reason, the risk of someone stealing your personal information or logging in illegally is greatly reduced.
Two-factor authentication has also been implemented in the Tsukaeru cloud service to protect the personal information of our customers.
7. Make it a habit to back up data
In the end, you are responsible for protecting your online privacy and digital data! However, it shouldn’t be something that you need to remember to do! Taking actions to protect your data on a regular basis should be a habit, especially for files, folders, and information that you use for work. It is very important to back them up properly to be prepared for unforeseen circumstances.
Choosing the right backup solution for you
When it comes to backup solutions, an essential component of data protection, the most important thing is to choose a solution with security and peace of mind. Tsukaeru Cloud Backup combines simplicity of use with the highest level of state-of-the-art security to create the perfect service for business backups. The all-in-one solution Tsukaeru Cloud Backup + (Plus), which integrates backup functions with security management tools, is also becoming more popular. Please visit the links below to learn more.
Click here for details of the Tsukaeru Cloud Backup service.
Click here for details about Tsukaeru Cloud Backup + (Plus).
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00




.jpg)

.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
(1).jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
_2(1).jpg)
.jpg)
.jpg)
.jpg)
.jpg)
