Data is truly the lifeblood of modern business. Needless to say, this makes backups an essential part of company security measures. With an increasing reliance on data, more and more organizations have realized its importance and now have some form of backup system.
However, are you sure that your company’s or department’s backup strategy is sufficient? Unfortunately, many companies’ data backup strategies have not yet reached the level of “truly reliable” nor are capable of dealing with all the current risks and challenges.
In this article, we will look at four reasons why companies may need to rethink their backup strategies right now.
1. Data disaster risks are increasing every year.
Companies face growing risks of losing data. For a “normal” data incident that could happen in daily life, normal backup options may be sufficient. However, those measures will not be enough to deal with larger threats, such as natural disasters, theft, or cyber attacks.
In Japan, which is prone to natural disasters, such as earthquakes, typhoons, fires, and flooding, data loss to such unpredictable events is a definite possibility. If a major data incident occurs, it can have a devastating impact on your business. For the best possible protection, every company should consider adopting cloud backup services.
2. There is a growing threat of cyber attacks.
Cyber attacks are, sadly, no longer a rarity in the business world. Globally, countless new malware programs are detected every day, and 36% of all cyber attacks target small- and medium-sized enterprises (SMEs). According to a report by the Tokyo Metropolitan Police Department released in September 2021, 66% of ransomware victims were SMEs. In addition, 39% of those attacked reported that investigative and recovery costs exceeded 10 million JPY. The evidence is clear: cyber attacks are a very real and imminent threat.
.jpg)
Case study: Hackers send spam emails from FBI account
No matter how well you take precautions, unfortunately, it is still possible to fall victim to a well-designed cyber attack.
On November 13, 2021, hackers gained unauthorized access to the external email system of the FBI (the United State’s Federal Bureau of Investigations), considered to be one of the most secure organizations in the world, and were able to send tens of thousands of emails from an FBI email account. Although no malware was attached to the emails, it should not be so easy for professional hackers to break into a supposedly secure system.
This incident demonstrates how important it is for SMEs to protect themselves with secure backups.
Additional reasons for backups
Cyber attack preventative measures are not the only reason you should have backups.
3. Hardware failure is inevitable.
Traditional hard drives and tapes, which play a major role in many companies’ local backups, will eventually reach the end of their useful life. In addition, hard drives are very delicate recording media and can easily fail due to a variety of problems.
Relying on such a potentially risky backup method considerably increases the risk of data loss. In order to protect your data as securely as possible, it is extremely important to create a backup environment that does not rely solely on a local hard drive.
4. Technological advancements are accelerating.
Technology and trends are evolving and changing at an ever accelerated pace. According to a 2020 study conducted by Dell Technologies, the amount of data managed by companies has increased by 40% since 2018 and by 831% since 2016. Data management for companies will only continue to increase exponentially, and in order to keep up in terms of data volumes and technological advancements, companies must constantly replace and improve their equipment and systems. Therefore, choosing a backup system that is flexible and scalable can greatly reduce the time and financial cost of staying updated and secure.
.jpg)
Daily backups: Lifeline in time of emergency
In one case study, a clicked link in a spam email installed ransomware software on an office computer. Soon, the company’s files on their server were encrypted and inaccessible.
The cybercriminals demanded a large amount of money from the company to regain access to the files. However, even if the ransom was to be paid, there was no guarantee that the files would actually be unencrypted. Therefore, the company contacted their cloud backup service provider and asked if they could help. Luckily, the cloud backup service provider was able to successfully restore all the data, and the ransom went unpaid.
How to respond to a cyber attack
If your computer or company has fallen victim to malware or a ransomware attack, the first step is to suspend your regular backup program. If you continue to backup your data as usual after the infection, there is a risk that pre-attack files will be overwritten by the infected or encrypted files.
If you have been backing up for a long period of time, you will have created multiple copies of your data, each of which will increase the chance of success of restoring your files.
It is imperative that you act now to protect your company and data from ever-evolving cyber threats.
.png)
Tsukaeru Cloud Backup
Regarding the four risks discussed so far, cloud backup is the most effective way to protect your data and company. For many companies, there is an urgent need to review and update their backup strategies. We highly recommend that you consider Tsukaeru Cloud Backup for a complete and reliable backup solution.
Protect corporate data from the ground up with advanced security
Tsukaeru Cloud Backup is the most powerful solution to protect your corporate data against natural disasters, hardware failures, and cyber attacks. With no required technical knowledge or complicated installation, the service can be easily set up in five minutes and ready for data restoration on a file-by-file basis.
The low price of 1,408 JPY per month (two-year contract) includes a 200 GB capacity for one PC and up to three mobile devices.
To experience the benefits of cloud-based backup, please contact us below for a free trial of Tsukaeru.net’s Tsukaeru Cloud Backup service.
Click here to learn more about Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
With the infection rates of COVID-19 seemingly settling down, the expectation is that more and more people will start to go on sales and business trips again, slowly returning to their pre-pandemic business lives. However, when traveling, there are times when you cannot pull out your laptop to access the information you need. This is where smartphones come in handy.
With the proliferation of cloud-based file sharing and increasingly powerful mobile devices, it is becoming possible to handle more and more complicated tasks on the go. However, many people are reluctant to do so due to security concerns.
In our most recent blog, we will look at the current status of smartphone usage for doing business and discuss the benefits of working with cloud-based mobile applications.
Do you use your own smartphone for work?
Penetration rate of smartphones for business use
According to a survey of company employees in Japan conducted in 2017, while laptops were often provided by their companies, there were few instances where smartphones were also provided. In the majority of cases where smartphones are used for business purposes, employees use their own personal devices for work, a concept called “BYOD” (Bring Your Own Device).
In Japan, many people have security concerns with BYOD in a work context. However, due to the COVID-19 pandemic, many companies had no choice when switching to remote work. Already dealing with the initial cost of providing laptops, these companies were unable or unwilling to provide smartphones in addition. Another concern was requiring employees to juggle two mobile devices at the same time: one for personal use and one for business.
For these reasons, BYOD is being adopted overseas more so than in Japan and has led to improved productivity and services. For example, Wal-Mart, the largest supermarket chain in the U.S., introduced BYOD in October 2018. By downloading a dedicated app to their smartphones, employees can report to work, manage their schedules, and search for products using a voice assistant, leading to improved work efficiency.
.jpg)
Improved work efficiency with smartphones
Takafumi Horie, the Japanese entrepreneur who founded Livedoor, says, “I don’t need a computer anymore. I can work and earn money wherever I am with my smartphone.” He does everything from contacting people to writing manuscripts using only his smartphone. Of course, not everyone can earn as much as he does, but with the rapid development of digital technology and communication systems, it is becoming possible to work with restrictions based on time and space. The number and type of tasks that can now be completed with mobile devices have increased dramatically over the years, and in particular, cloud-based file-sharing services have made it possible to easily access and exchange large amounts of data, something which is difficult to do with email.
Best file sharing solutions for businesses
While it is possible for nomadic workers to work from their smartphones, there are still many hurdles for companies to overcome when implementing such systems. Considering the security risks involved, it is easy to understand why companies are cautious about adopting cloud-based file-sharing services.
Cloud-based file sharing service usage
According to the 2021 White Paper on Information and Communications by the Japanese Ministry of Internal Affairs and Communications, 68.7% of companies in Japan used cloud services in 2020, up four percentage points from 64.7% in 2019. Between 2016 and 2020, up to 70% of companies have started using cloud services, indicating that corporate awareness of cloud services has changed significantly.

Key points for corporate cloud use
According to the above white paper, 87.1% of the companies that use cloud services reported that it was “very effective” or “effective to some extent,” indicating that they could see the benefits regardless of concerns about security or other issues.
So, how did the companies use cloud services? In looking at the results, it can be seen that “File storage/data sharing” was the most popular at 59.4%, followed by “Email” (50.3%), and “Internal information sharing/portal” (44.8%). More advanced usage functions, such as “Sale support” (17.6%), “Production management” (10.2%), and “Billing and payment systems” (8.0%) remained at low levels. In other words, the results show that Japanese companies are actively exploring how they can improve their business efficiency with cloud-based tools such as file-sharing.
Tsukaeru FileBako for mobile use
While there are many cloud-based file-sharing services, Tuskaeru FileBako from Tsukaeru.net is a popular choice of many small- and medium-sized companies because of its ease of use and low implementation cost. In addition, the ability to use the service on mobile devices is an attractive benefit for those companies engaged in remote work and similar activities.
Download the mobile app
With the RushFiles app, available both on the Apple Store and Google Play, users can log in and immediately start using Tsukaeru FileBako on their smartphones and mobile devices.
.png)
Easy syncing and file sharing with your smartphones
When you’re on the road and need to quickly share files or check their contents, your smartphone can be your best option. For the same price, there is no limit to the number of users, whether 100 or 1,000, and no additional costs if the number needs to increase. With a default capacity of 1 TB, the monthly price starts at 10,780 JPY (tax included, three-year contract).
To experience the benefits of cloud-based file sharing on smartphones and mobile devices, please contact us below for a free trial of Tsukaeru.net’s Tsukaeru FileBako service.
Click here to learn more about Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
Hard disk drives (HDD) and solid-state drives (SSD) are common data storage devices and are growing in capacity and speed as the technology evolves. While these increases and lower prices benefit users, there is still one major risk: losing all your data at once if the HDD or SSD fails.
As data is always at risk from malfunctions, viruses, malware, and other disasters, backups are essential for data protection. In this article, we’ll take a deeper look at backups and their importance.
Backups are important, but…
Of course, we all know the importance of backups. However, it can be a real hassle to set up, and there are more pressing things to do. I’m sure you’ve found yourself thinking, “It’s fine. Nothing is going to happen. I’ll just do it later.”
30% of people have never backed up their data!?
According to one survey, about 30% of people in the U.S. said that they have never backed up their data before. Even though so much data is stored on computers and smartphones, the reality is that many people still have no experience or understanding of backing up their data.
The current state of backup in Japan
Now that smartphones have similar storage capacity as computers, protecting data, especially important information such as address books, photos, and videos, on mobile devices is becoming equally important. However, a survey conducted by TIME & SPACE in 2020 in Japan found that 40.4% of respondents indicated that they “Don’t keep backups.” In terms of explaining why, 29.2% chose “I don’t know how,” 27.0% chose “It’s too much trouble,” and 17.7% chose “I’ve never bothered.”
.jpg)
Why should you backup your data?
It can be surprising how many people in the U.S. and Japan do not back up their data. Especially in the case of smartphones, important and irreplaceable data can be lost, and there is a strong possibility that it can never be recovered.
Given the situations described below, the risk of data loss is ever increasing.
Japan: High risk of disaster
While Japan is blessed with an abundance of beauty and nature, it is also a country that is prone to natural disasters that can wreak havoc.
For example, with only 1% of the world’s landmass, Japan has 20% of the world’s earthquakes (magnitude 6.0 or higher).
In addition, recently the risk of flooding and landslides due to climate change and urbanization has also increased. The frequency of short-duration torrential rainfall with precipitation of 500 mm or more per hour has increased almost 1.4 times in the last 10 years as compared to the ten years between 1976-1986.
The Japan Meteorological Agency warns that if climate change continues at current rates, the number of days and frequency of heavy rainfall will be 20 times higher by the end of the century. Whether a company or an individual in Japan, it is essential to be prepared for the risk of data loss given these risks.

Cyber attacks and malware on the rise
On October 31, 2021, more than a dozen printers in a Tokushima Prefecture hospital, without warning, started printing at the same time. They produced an identical message, “We stole and encrypted your data. If you don’t pay the reason, we’ll disclose the data.” Due to the ransomware attack, the medical records of 85,000 patients were suddenly inaccessible.
The number of attacks like the one above is increasing. 33.8% of companies in Japan reported that the number of cyberattacks in April 2020 had increased as compared to the same month the year before, much higher than the 5.9% who reported that the number was lower. Cyber attacks are on the rise due to the spread and expansion of remote work, digital transformation (DX) in society as a whole, and the increased use of IoT devices.
.jpg)
The inevitable “life span” of a computer
On top of the risks of disasters and cyberattacks mentioned above, another possibility is HDD failure.
How long will a computer last?
As a computer’s lifespan depends on the main unit and the conditions of use, it is difficult to know how long it will last. However, five years is considered to be the life expectancy for a computer, while an internal HDD is four years. An external HDD is even shorter, about three years (about 10,000 hours). HDDs are designed to read and write data on the surface of a disk, which wears down over time. The lifespan of a disk may be even shorter in an environment with high humidity and room temperature.
SSDs, on the other hand, have no moving parts and on average last for about five years. In either case, the end of the lifespan for a computer or storage drive will eventually come.
Regular backups are the safest choice!
For peace of mind, the best option is to back up your files and data on a regular basis so you do not panic if something suddenly happens.
While there are a variety of ways to back up your files and data, such as an external HDD, the safest and most recommended way is to use cloud storage. With a cloud backup service, automatic backups save your important files and data to a secure, remote server. Compared to other methods, this is the easiest and more reliable method.
Tsukaeru Cloud Backup
Provided by Tsukaeru.net, Tsukaeru Cloud Backup is a popular cloud backup choice of many small- and medium-sized businesses due to its high-cost performance and ease of implementation compared to competitors.
Various backup options for files, data, and even entire OS
Tsukaeru Cloud Backup is the most powerful solution for data protection from natural disasters and cyberattacks.
For backups, we offer fast and reliable restores for problems with applications, systems, and data on any device.
In addition, your data is protected with complete security measures that detect risks before they occur.
The 1,408 JPY per month (two-year contract), including a 200GB capacity for one computer and up to three mobile devices, offers an easy way to implement a cloud storage system at a low cost.
A free trial is also available to experience Tsukaeru.net’s Tsukaeru Cloud Backup service.
Click here to learn more about Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
Recently, the term “DX” (Digital Transformation) has been appearing frequently in discussions about how the business world is changing. While many of us may have an idea of the importance of digital technology for businesses, the differences between DX and IT may not be that clear.
In this article, we will discuss DX in order to deepen your understanding of the concept and show how it can be applied to your company’s growth strategy, using specific examples.
What is DX (Digital Transformation)?
According to a survey conducted in Japan in July 2021 by INDUSTRIAL-X, a DX support services company, more than half (52.2%) of 500 managers (or higher positions) surveyed said they did not know what DX was. Of those surveyed, 30.2% had heard of the term, and only 17.6% actually knew what it was.
Despite many companies introducing remote work in response to the COVID-19 pandemic and relying more than ever on IT, it is obvious that awareness of DX and its importance is extremely low in the business community.
Defining DX
So, what exactly is DX, anyway?
According to the “DX Promotion Guidelines Ver. 1.0” published by the Japanese Ministry of Economy, Trade, and Industry (METI) in December 2018, it is defined as “the transformation of products, services, and business models based on the needs of customers and society, as well as the transformation of business operations themselves, organizations, processes, and corporate culture and climate, in response to rapid changes in the business environment, using data and digital technologies to establish a competitive advantage.”
Based on this definition, you can see that DX is when a company uses IT to fundamentally transform its organization.
Reasons to implement DX
However, according to the above-mentioned survey, nearly two-thirds (59.4%) of the total respondents, answered that they had "no intention" to implement DX. The reasons given were "I don't know how to proceed or what approach to take" (25.6%), "I don't know the effects or objectives" (21.7%), and "I don't know what I want to achieve" (19.7%), indicating that a lack of understanding of DX is hindering its promotion in the first place.
Nevertheless, according to a METI report, the shortage of IT personnel in Japan is expected to expand to approximately 430,000 by 2025 if DX continues to be ignored. Furthermore, it is estimated that older systems with outdated technology will account for 60% of the total, resulting in an annual economic loss of up to 12 trillion JPY between 2025 and 2030. Conversely, if DX was widely implemented now, it is predicted to boost real GDP by about 130 trillion JPY by 2030.
.jpg)
Differences in perceptions of DX
According to the same INDUSTRIAL-X survey, the most common answers for the purpose of DX initiatives were “cost reduction” (48.5%) and “quality and operation improvement” (30.5%). Despite the METI stated purpose of “establishing a competitive advantage,” it is clear that many people view DX in much the same way as IT: for the purpose of improving operational efficiency.
Does introducing IT create DX?
The goal of DX is transformation through the use of data and digital technology. However, if IT is introduced solely to improve business efficiency, it is not DX. In other words, DX is the goal, and the use of IT to achieve that goal is merely a means to an end.
The METI DX Promotion Guidelines, mentioned above, also state that “in order to achieve DX, it is essential to have a management strategy for transforming the business using digital technology, a strong commitment from management, and a structure and system within the company that includes a change in the mindset to implement the strategy. The most important thing is to have a clear vision of “What do you want to change and how?” by using data and digital technology.
DX case studies
Matsushiro Industrial Co., Ltd. is a well-established company that has been producing electronic components, precision sheet metal, and paint since 1958 and has been a leader in manufacturing in Nagano Prefecture for many years. In order to fundamentally improve their business processes, the company started using Tsukaeru FileBako from Tsukaeru.net to easily exchange files and use cloud storage for their data needs. Matsushiro Industrial Co. Ltd. is an excellent example of a company that has embraced DX by boldly adopting new values and technology, while at the same time valuing the accumulation and succession of technology and know-how.
.jpg)
Click here for the full Matsushiro Industrial Co. Ltd. case study (only in Japanese).
Raymay Fujii Co. Ltd. is another excellent example of DX. Founded in Kumamoto in 1890, it has built a network of offices covering the entire Kyushu region and is a “complex company that supports a wide range of intellectual production services” that is developing a wide range of businesses as a trading company and stationery manufacturer.
The 2016 Kumamoto earthquake was a turning point for the company in terms of realizing the importance of cloud computing and the quality of service. After the earthquake, because many employees were unable to go to their physical offices, there was an urgent need to create a system that would allow them to work remotely. However, the cloud server that they initially installed was unstable and unreliable, as the system went down every time there was an OS update. Switching to Tsukaeru FileBako, they were “blown away” not only by the high stability but also the low cost and ease of use. In this situation, cloud storage played a vital role in helping Raymay Fujii Co. Ltd. continue its 130-year evolution as a business.
(2).jpg)
Click here for the full Raymay Fujii Co. Ltd. case study (only in Japanese).
Data utilization in the sports industry
One industry that has seen a remarkable shift to DX is the sports industry. This is especially true in the U.S. Major League Baseball (MLB), with the introduction of a system that tracks the speed and rotation of pitches, the launch angle and estimated distance of batters, and the movements of players on the baseball field.
(1).jpeg)
The possibilities of sports x technology
In the past, the strength of a team was largely determined by each player’s ability and the coach’s experience. However, IT has now made it possible to collect vast amounts of information in real-time, and how that information is analyzed and utilized can change the outcome of a game. As a result, there is a need for experts who can analyze data with a high degree of accuracy and create a system to share the results within the team.
For example, one of the reasons for the success of the Japanese national team in the 2019 World Cup Rugby tournament was due to data analysts who quantified and analyzed game video footage, each player’s speed and power, and scrum formations in order to gain the upper hand on the rugby pitch.
Tsukaeru.net’s partnership with the Shinshu Brave Warriors
Tsukaeru.net has signed a partnership agreement with the Shinshu Brave Warrior professional basketball team based in Nagano City and Chikuma City, Nagano Prefecture. Providing not only high-quality and stable cloud services, Tsukaeru.net will also support the team’s DX implementation from a technical perspective by making full use of the cloud service.
(2).jpg)
Click here for press release (only in Japanese).
Tsukaeru FileBako
Tsukaeru.net’s easy to use and inexpensive Tsukaeru FileBako has been chosen by many small- and medium-sized companies to help them with DX implementation.
Ideal for DX: Easy to use, unlimited users, and advanced security features
One reason why Tsukaeru FileBako is so easy to use is that there is no need to use a special interface, allowing you to simply upload and download data through the Explorer browser in Windows. Also, with unlimited users, the fee is the same whether you have 100 or 1,000 users. There is no need to worry about user billing or issuing privileges even if employee numbers increase. Furthermore, access permissions can be set for each folder, allowing safe and secure communication with external parties, such as business partners. With a default capacity of 1TB, the monthly price starts at 10,780 JPY (tax included, three-year contract).
A free trial service is also available, so if you are thinking of introducing a cloud storage service, please feel free to contact us at your convenience.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
More and more companies are embracing the cloud services due to its convenience and ease of use, and as file sharing is becoming an essential service for safe and easy data exchange, cloud computing is gaining even more popularity.
However, while cloud services offer many benefits to businesses, security can still be a major problem. Despite the obvious advantages of using the cloud, there are understandably some people with concerns about security and usability who are not ready to take the plunge. Therefore, when getting ready to implement cloud computing, it is extremely important to choose a reliable service provider. In this article, we will focus on three key points regarding security that you should always consider when choosing a cloud-based storage service.
1. Data center safety
When you use a cloud service, your data will be stored in the data center of the service provider. In terms of security, it is very important to check what safety and security measures are being taken in the data center.
One specific way to do this is to refer to the "Data Center Facility Standards" defined by the Japan Data Center Council. This set of standards was created to meet global realities but has been revised to address specific situations in Japan, such as its high levels of seismic activity. The standards are divided into four tiers (Tier 1 to Tier 4) and can be used to assess the service level of the data center.
As for data center location, you may wonder if domestic or international data centers are better. Each has its own advantages and disadvantages. In the case of Tsukaeru.net’s domestic data center, it is located in Nagano Prefecture, which is considered to be less susceptible to natural disasters due to its location and geographical features. Also, it is classified as the Tier 3 level standard in the aforementioned Data Center Facility Standards.
What is the Tier 3 standard?
・A higher level of safety is ensured against disasters, such as earthquakes and fires, than in regular buildings.
・Redundant facilities are in place that can continue to provide computing services even if some facilities are temporarily shut down, such as for equipment maintenance.
・Access control to the building and server room is implemented.
・Operation reliability for assumed end users is 99.98% or higher.
Location affects data transfer rate
Data transfer speed can also be affected by the location of the data center. Although the actual specs can differ depending on each cloud service, as your data is actually stored in one physical location, the distance between you and your data can be an important factor in terms of speed and usability.
In this regard, the Tuskaeru.net data center is ideally located in Nagano City in Nagano Prefecture in central Japan, where our head office is also based.
.jpg)
2. Service management system
In the cloud storage industry, there are a variety of ways that businesses manage their data storage and server maintenance. In order to avoid the risk of information leaks or compromise, it is recommended to choose a service that has the full range of information security measures and network redundancy.
Tsukaeru.net provides 24-hour support and complete security measures
Tsukaeru.net customer service is always available by telephone or chat from 10:00 to 17:00 (JST) to address your questions and concerns. Of course, you can contact us by email at any time.
In addition, in case of server downtime as a result of server trouble or hardware failure, emergency calls are accepted 24 hours a day.
In addition, Tsukaeru.net has achieved stable operations with the highest standards of security policy, utilizing more than 20 years of experience in providing hosting services, such as network redundancy and in-house power generation facilities, in addition to thorough security measures certified by ISO27001 (ISMS).
3. Data transfer encryption
Encryption is an essential part of cloud service security. Instead of transferring data in its “raw” state, it is encrypted with one or more mathematical techniques and a password to maintain data confidentiality. As it is one of the strongest ways to keep your data safe, it is highly recommended to choose a service with the most up to date encryption.
What is AES-256?
In a nutshell, AES is one of the various methods of "encryption.” AES (Advanced Encryption Standard) is a new encryption technology that was approved by the National Institute of Standards and Technology (NIST) in 2001 that has become the current standard encryption algorithm for communication data.
AES uses "symmetric key cryptography," in which the same encryption key to encrypt and decrypt (undo what has been encrypted) is applied. In this case, the longer the cryptographic key data used for encryption and decryption, the more secure it is. The length of the cryptographic key is called the "key length" and is generally expressed in "bits."
The previous standard was called DES (Data Encryption Standard), which had a shorter key length of 56 bits and was vulnerable to brute force attacks. In comparison, AES has a longer key length than DES, with a choice of 128, 192, or 256 bits. In other words, AES itself is the most secure encryption technology as of 2021, and AES-256, which has the longest key length, is the strongest encryption method at present.
Tsukaeru FileBako provides security and peace of mind
Tsuskaeu FileBako, a file sharing service for corporations provided by Tsukaeru.net, uses AES-256 encryption to ensure the best protection and privacy for our clients. In addition, it also employs two-factor authentication and SSL for the web management screen, providing even greater security to keep your valuable data safe.
.jpg)
Easy and secure cloud adoption with Tsukaeru FileBako
Choosing a reliable and secure service provider can be one of the most important steps when implementing a cloud computing system. With a service that provides a solid data management system, you get all the advantages and convenience of the cloud without having to worry about security.
Tsukaeru FileBako manages data with a system that puts security front and center. Our servers are operated and maintained by skilled and dedicated staff at our own domestic data center, and your data is protected with the latest encryption technology from storage to transfer. While not only focusing on security, this service also offers an unlimited number of users and a large, 1TB capacity for as low as 10,780 JPY per month (tax included, 3-year contract), a high cost performance ratio that makes it a popular choice for many businesses.
To find out about our exciting free trial offer, please contact us using the link below.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
With ever expanding digital transformation (DX), a company’s data also increases in volume and value. As a result, data protection is one of the top priorities for any company. This is especially true for companies located in Japan who need to prepare for two dangers that threaten their data security: natural disasters and cyber attacks. In this article, we will discuss the urgency of these threats and the preventative measures that should be implemented.
Japan: One of the most disaster prone countries in the world
While it goes without saying that Japan is a disaster-prone country, there are still many people who think that they and their companies are safe from the risks. However, based on historical records and research, the government and many scientific organizations are well aware of the risks and do their best to educate people about them. Business people operating in Japan would be well advised to pay attention to the following facts.
A history and future of disasters
・The probability of a Southern Ocean Trough earthquake is 70-80% over the next 30 years.
・The probability of a severe tremor (6 or higher on the Japanese “Shindo” scale) within 30 years in metropolitan Tokyo is 47%, 38% in Yokohama, 46% in Nagoya, and 30% in Osaka.
・Although the probability of future earthquakes in Tohoku and the Sea of Japan is relatively low, they have occurred in the and caused significant damage (e.g., the Niigata Chuetsu Earthquake and the Tohoku Earthquake in 2011).
・Flood damage in Japan in 2019 totaled 2.18 trillion JPY, the largest recorded amount of non-tsunami flood damage in a single year
・In August 2021, the Japan Meteorological Agency (JMA) issued a “Special heavy rainfall warning” and “General information on significant heavy rainfall due to the occurrence of linear precipitation zones in various areas. In Northern Kyushu, some areas reached 50% of their annual rainfall in less than a week in that same month.

Cyber attacks: “Disasters” in the digital world
In addition to real world disasters, there is another risk that companies should be wary of: cyber attacks. These digital disasters threaten more than just corporate data. The ransomware attack on the Colonial Pipeline fuel company earlier this year and the damage it caused to human lives and social infrastructure is still fresh in our minds.
Ransomware damage
According to the August 2021 “10 Major Security Threats 2021” report from the IPA (Information-technology Promotion Agency, Japan), “damage from ransomware” is considered to be the largest threat for organizations.
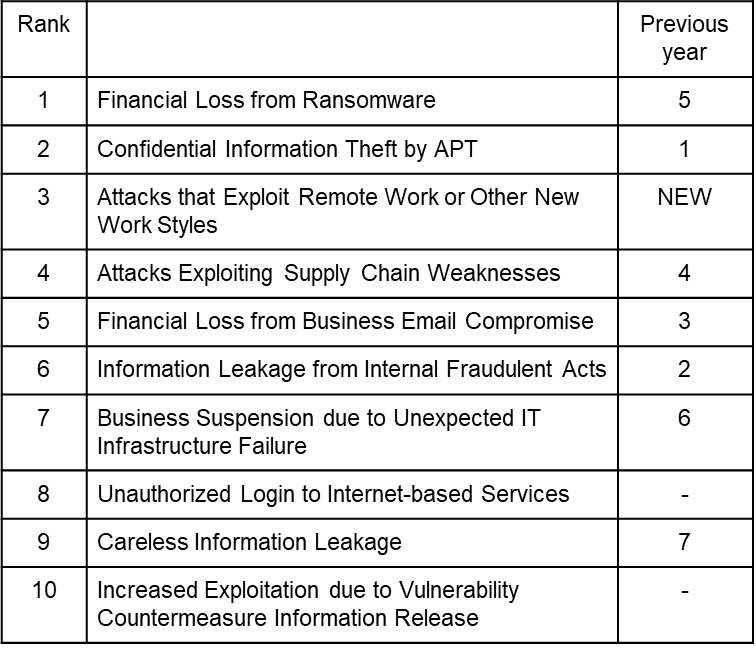
Source:”10 Major Security Threats 2021” / IPA(Information-technology Promotion Agency)
https://www.ipa.go.jp/security/vuln/10threats2021.html
Ransomware is a virus-based cyber attack that encrypts the data stored on a company’s computer or server. or renders the device itself unusable. It is an extremely malicious cyber attack in which money or encrypted assets are demanded in exchange for data recovery or for not exposing confidential information.
In fact, according to data released by the Tokyo Metropolitan Police Department in September, ransomware attacks in the first half of 2021 increased by nearly three times compared to the second half of 2020. Of the affected companies, nearly 40% incurred a total of more than 10 million JPY in investigation and recovery costs.

Ransomware damage and attack routes in Japan
According to the Metropolitan Police Department report mentioned above, the routes of ransomware infection are through VPN devices (55%), remote desktops (23%), suspicious emails with attachments (13%), and others (10%). As companies have responded to the COVID-19 pandemic by implementing remote work and relying on remote desktops and VPN devices to allow outside connection to company networks, hackers are increasingly taking advantage of the disruption.
Keeping your data safe
The above information is a sobering reminder of the threats that corporate data faces in 2021.
However, companies should not let the fear of future possible threats derail their plans. Instead, they should take proactive and preventative action now.
Disaster countermeasures
One excellent way to prepare for natural disasters is to store company data in the cloud. By storing the data in a location that is both unlikely to be affected by a disaster and that is protected even in the event of a disaster, companies can easily restore their data to existing or new computers and devices. In addition, it is possible to retrieve only the necessary files and folders from the cloud back-up data to get up and running again.
Ransomware countermeasure
As a general rule, the best defense against cyber attacks should be mult-ilayered. As security threats are diverse and ever changing, it is possible to be better prepared for all kinds of risks by implementing overlapping defenses. Specifically, firewalls and WAFs should be installed to prevent intrusion from the outside and internal security systems should be created.
To be better prepared against ransomware, one of the most alarming cyber attacks, please follow the three following steps.
■Prevent intrustion
・Always update security software, operating systems, and major software
・Do not click on suspicious links or pop-ups, and do not open suspicious emails
・Use trusted websites
■Prevent attacks
・Use the latest security products and procedures
・Do not involve those with administrator authority in daily operations if possible
■Recovery
・Regularly backup data and systems
・Maintain at least one offline data backup

Tsukaeru Cloud Backup
Finally, an effective solution to protect your data from two ever present threats to your company and your data: natural disasters and cyber attacks.
Cloud Backup protects your data with the best security measures
Tsukaeru Cloud Backup is the most powerful solution that combines backups as a natural disaster countermeasure and security as a cyber attack countermeasure.
Backup protocols provide quick and reliable restoration for all incidents that affect applications, systems, and data on any device.
Security protocols detect threats before they occur and protect data with full security measures.
For a low cost of 1,408 JPY per month (two-year contract), Tsukaeru Cloud Backup provides a 200GB capacity service for one personal computer and up to three mobile devices.
To find out about our exciting free trial offer, please contact us using the link below.
Click here for more information on Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
The idea of "vulnerability" in regards to the Internet has been making an appearance on TV and in the media with increasing frequency. You may have seen headlines such as "ABC company's customer information was leaked" or "1,000,000 customer’s credit card information compromised in a cyber attack."
For Internet-based services, this is always a risk. The reality is that this is no longer only a problem for large corporations. Now small- and medium-sized enterprises (SME) have become targets of cyber attacks targeting known and new vulnerabilities.
In this article, let’s look at the basics of vulnerabilities that corporate webmasters and those who handle Internet services for business should know.
What is a vulnerability, anyway?
A vulnerability in this context is a security flaw in a software program or a computer network/system. Your first reaction may be, "Well, why don't they just create better security by making software without flaws?" Unfortunately, this is practically impossible. The amount of computer code that makes up software is enormous, and since that code is written by human hands, it is extremely difficult to create perfect software with no flaws at all.
Vulnerability exploitation: The fallout
A cyber-attack that successfully targets an unaddressed vulnerability can lead to serious damage such as a leak of personal information or website tampering. However, the results can be even more damaging and harder to repair. A security compromise can easily create a lack of trust from your customers and a long lasting, negative reputation, a death blow to many businesses.
As mentioned above, cyber-attacks are also becoming a growing problem for SMEs. One reason is that SMEs usually have smaller staff than large corporations with well-developed information system management departments and are less likely to have much time and money to spend on security measures and communication with providers, all resulting in greater vulnerabilities.
.png)
Cyber attacks: Types and examples
According to a report by the Security Center of the Information-technology Promotion Agency, Japan, cyber-attacks are included among the 10 major information security threats for organizations in 2021, for example, "Ransomware damage (No. 1)," "Confidential information theft from targeted attacks (No. 2)," "Attacks targeting new work styles, such as telework (No. 3)," and "Increasing exploitation of countermeasure information vulnerability after release (No. 10).”
Perhaps of greatest concern is the increase in cyber attacks targeting remote work employees. While remote-work security issues have been discussed previously, the percentage of remote workers has rapidly increased, as well as vulnerability exploitations. For example, in July 2020, a vulnerability was discovered in the web conferencing service ZOOM that allowed access to private meetings. Furthermore, in August 2020, a VPN product vulnerability was exploited to steal approximately 900 credentials and publish them on the Internet.
Preventative measures against cyber attacks
In order to minimize the possibility of cyber attacks that exploit vulnerabilities, we recommend that you enforce the following three ironclad rules of security on a daily basis.
.png)
Educate yourself
First of all, the most important thing is to have the best and most current information about security and vulnerabilities. If you are in charge of IT at your company, it may be a good idea to get advice from an expert or regularly read up on changes in the industry, new developments, and what the bad guys are doing.
Perform system updates
Always keep your operating systems (OS) and software updated, which contain not only enhancements but also fixes for vulnerabilities and bugs. Continuing to use an older OS is a significant security risk. However, in recent years, there has been an increase in the number of “zero-day” attacks, in which a vulnerability is discovered and exploited before the fix is distributed. This is just one reason why It is important to keep up with the latest security information to mitigate risks as much as possible.
Use a service with strong vulnerability countermeasures
While system updates and keeping up with the latest information are essential, you can also use services that are strong in protecting against vulnerabilities. For example, one such service is a Web Application Firewall (WAF), a network security system that protects customer and credit card information from cyber attacks targeting web application vulnerabilities.
It is also important to introduce a reliable cloud tool with basic security features such as backup and malware protection for remote work.
.jpg)
Tsukaeru Cloud Backup + Vulnerability Protection
Tsukaeru Cloud Backup+ (Plus) from Tsukaeru.net not only provides cloud backup functionality but also provides complete vulnerability countermeasures.
Virus detection with data scan
Tsukaeru Cloud Backup+ automatically scans for viruses and protects against malware lurking in your backups. If an infected file is found, it will be prevented from being restored from the backup, minimizing any damage.
Automatic vulnerability assessments
No matter how hard you try to keep up to date with the latest information and developments on vulnerabilities, there is a limit to how much you can do by yourself. Tsukaeru Cloud Backup+ automatically conducts daily vulnerability assessments, detecting problems that you cannot see before they occur and displaying the severity in using a color-coded system.
Tsukaeru Cloud Backup+ is an affordable service that provides both security management and cloud backup at the same time, with uncompromising security measures and ease of use.
To experience it for yourself, contact us to learn about our free, 14-day trial!
Click here for more information on Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
Synology integration is an option that allows the automatic synchronization of data between Tsukaeru FileBako cloud storage and a NAS (Network-attached storage) device once every five minute. This combination makes it possible to create a data management system that protects your data, whether stored online or on hardware.
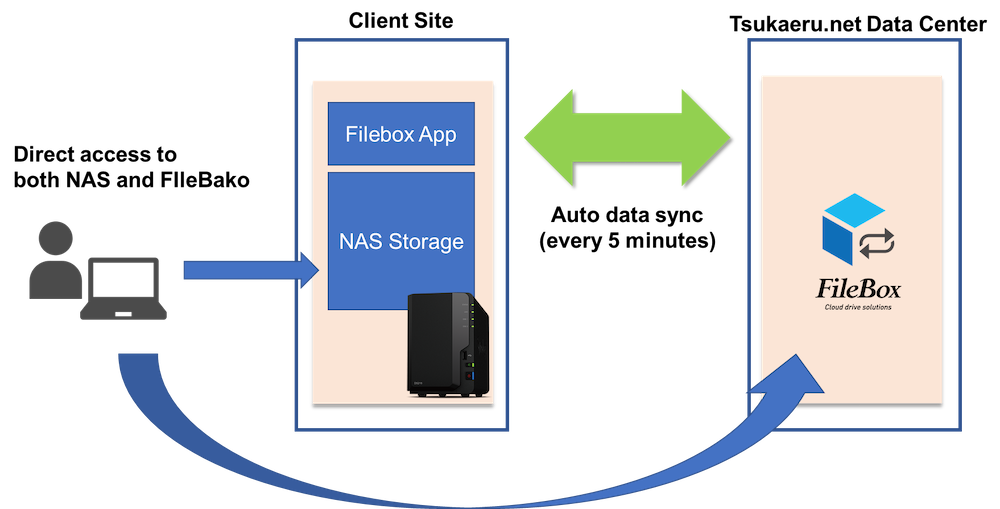
The demand for online file sharing is increasing as remote work becomes the new normal around the globe. Tsukaeru’s FileBako, a cloud-based, virtual drive service that allows users to upload data to and share it with an unlimited number of users, has been adopted by many companies due to its excellent cost performance and security. We have now developed a new synchronization option called Synology integration, designed to make Tsukaeru’s FileBako service even more convenient and secure to use. In this article, we will provide a detailed explanation of its background, new feature overviews, and setup process.
Tsukaeru FileBako is an amazing service that allows users to upload documents, images, videos, and other data to a cloud-based virtual drive. In addition, there is no limit to the number of users who can use the system to share data, and it can be used with various operating systems. Its low price also makes implementation easy and affordable for small- and medium-sized businesses.
Tsukaeru FileBako main features
・Unlimited number of users and unlimited use of 1TB
Additional capacity is available as a paid option
・Saves computer space
Download only the data you need to save space on your local device
・AD (Active directory) integration
Centralized ID/password control and remote management (paid option)
・Can be used with Windows Explorer and Mac Finder
・Available as a browser version and mobile app, allowing easy data sharing in the field or on the road
・Mail gateway function
Automatically uploads scanned data from multifunction devices, such as a scanner, to FileBako (paid option)
・Reliable security measures
AES 256-bit encryption, the world’s most secure encryption algorithm, two-factor authentication, and SSL for the web management screen ensure security
・Fast and reliable customer support
Support is available 24 hours a day by phone, email, chat, etc. in case of emergencies such as server downtime

What is NAS?
NAS stands for “Network-attached storage” and is an external data storage device that is specialized for use over a network. Compared to regular file servers, it offers lower installation costs and does not require personnel for management and maintenance. Synology Inc., which Tsukaeru has partnered with through the KSG Corporation, is a Taiwanese NAS manufacturer with global operations. Its 50% share of the European and US NAS markets make it a trusted and popular brand.
What is the new Synology integration option?
Development background
Both the Tsukaeru FileBako cloud service and Synology’s NAS are both popular choices, but each has their weaknesses, such as possible network failure with the former and downtime due to physical failures, disasters, or restoring backups with the latter. To provide even more peace of mind, we have jointly developed Synology integration, a new option that became available as of July 15, 2021.
.jpg)
Easy setup
1. [Customer side] Tsukaeru FileBako account creation
2. [Tsukaeru, KSG] NAS device setup and delivery
3. [Customer side] NAS device activation (after delivery)
NAS ancillary services
・KSG Corporation will ship the NAS device pre-set for use with Tsukaeru FileBako
・Hardware maintenance (9:00-17:00 weekdays, on-site the next business day for five years)
・Remote recovery option (9:00-17:00 weekdays for five years)
Summary
The Synology integration option synchronizes data between cloud storage and the NAS device in the on-premise environment every five minutes, creating a solid, safe, and secure system.
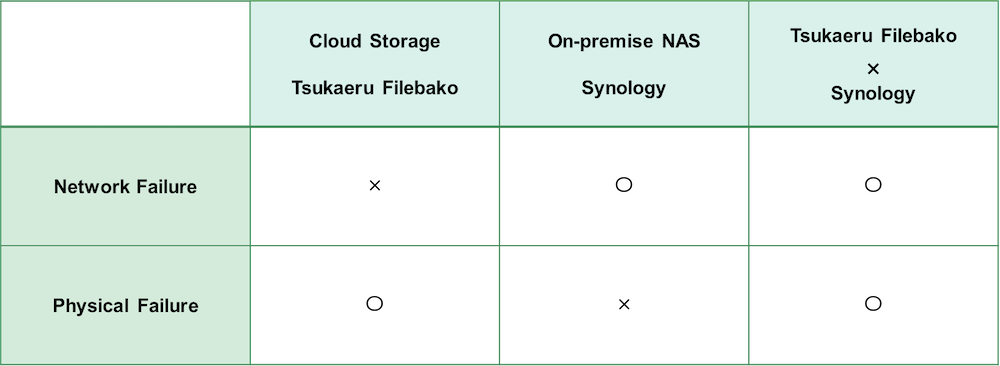
Tsukaeru FileBako’s new option keeps your data safe at all times
Tsukaeru Filebako and Synology integration together create an extremely convenient and secure combination. However, the only way to truly understand how it can meet your needs is to experience it for yourself.
With that in mind, we are happy to offer a free, 14-day trial period for Tsukaeru FileBako so you can see how it works.
*Synology integration is an option. To learn more, please contact one of our representatives for more details or to set up an online meeting to discuss it in person.
Click here for more information on Tsukaeru FileBako.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
In our current digital age, most of our data is now stored on computers, allowing us to easily access our files from basically anywhere at any time. It also frees us from the need to print and carry paper versions of the information. Gone is the worry about losing or forgetting important documents on the way to that important meeting.
However, just because the materials have been digitized does not mean they are 100% safe! Just as there are specific problems with paper documents, digital files have problems that are unique to that medium. One of those problems is data failure, and when it occurs, you can lose access to valuable information, or even worse, your data can be completely lost.
So what exactly is data failure and how can you prevent it from happening?
Data failure classifications and causes
Data failures can be categorized into two main types: physical failures and logical failures, each with a different cause.
Physical failure
Physical failure occurs when the parts of the hard disk are physically damaged and will not boot properly. This may happen if a hard disk is dropped or damaged by a natural disaster (ie., flooding). It can also occur if the physical parts wear out and fail during normal use.
When a physical failure occurs, you may hear the hard disk make strange noises, such as a "ticking" or "knocking" sound. It may also ask to be formatted during operation, freeze up, or reboot frequently.
A strange noise could indicate that you have a "magnetic head failure," sometimes called a “head crash.” This is the part of the hard disk that reads and writes to the data recording surface called a platter, and if this condition continues, the platter will be scratched, causing severe physical damage, which may make data recovery impossible.
Another possible physical failure is "firmware failure." For example, an electrical event may cause damage to the hard drive’s logic board, causing problems with firmware, the software that controls the device. This could result in data reading and writing being impaired. However, a firmware failure may be difficult to distinguish from the logical failure described below.
Logical failure
A logical failure is a situation where the hard disk itself is not physically damaged, but the data and folder structure stored inside is faulty. Signs that a logical failure has occurred can be files and folders that cannot be opened, file names that are rewritten without permission, or the appearance of a blue screen.
One of the causes of logical failure is mishandling or human error which causes data to be accidentally or maliciously erased, initialized, or formatted. Another cause is "file system failure," where the file system, which can be described as a file organizer, is damaged when the user forcibly terminates the system while in the act of writing data. The data itself may not be damaged, but it may suddenly become inaccessible.
.jpg)
What to do in the event of data failure
Although some of the symptoms of data failure are described above, without expert knowledge, it is not easy to determine whether it is a physical or logical failure. The more important thing is to identify the cause and take appropriate measures to prevent the symptoms from worsening and making data recovery impossible. To that end, it is highly recommended to follow these three following suggestions.
(1)Do not keep the power on
When a hard disk is experiencing a physical failure, the magnetic head will also continue to move while energized, further damaging the platter. Turning the power off immediately could stop your data from being completely destroyed.
(2)Do not keep turning the power on and off
Repeatedly switching the power on and off to check the operating status or reset the device may lead to further scratches on the platters or data loss as in (1) above.
(3)Do not disassemble
While you may want to disassemble the hard disk in an attempt to determine the cause, the inner mechanism is very delicate and any dust and dirt that may get in could worsen the failure. Also, disassembling the hard disk by yourself may void the warranty and any recourse from the manufacturer.
How can you reduce the chance of data failure?
Preventing physical failure
Due to the nature of physical failures, unfortunately, there are only a limited number of prevention measures that can be implemented. Hard disks are basically considered to be a consumable item with a limited life span. If used for a long time, it is inevitable that some kind of problem will occur. However, it is possible to reduce the chance of occurance to some extent by careful handling of the device or computer and replacing the technology every few years. In the industry, the lifespan of a hard disk is generally said to be three to five years, and it goes without saying that regular backups are necessary considering the impossibility of predicting when a physical failure will occur.
Preventing logical failure
On the other hand, there are several effective measures that can be taken to prevent logical failures, such as access rights management and virus infection prevention.
.jpg)
Access Rights Management
As mentioned above, human error or mishandling is a surprisingly common cause of logical failures. The risk can be significantly reduced by setting and managing the access permissions for each system’s functions and data. It is vital to always determine who actually needs a function or file and reconfirm/review the access permissions.
Virus infection protection
Anti-virus is not only about preventing logical failures; it is the foundation of information security. It is important to be able to update software and check for viruses on a regular basis with no hassle. Taking care of your security is directly related to protecting your important data.
Regular cloud backups provide assurance and peace of mind
While working to prevent data failures, it is equally important to take measures to minimize potential damage to your business in case of a data failure. The safest and easiest way to do this is to have backups, especially ones that use cloud services. With a cloud backup of all your files, you can minimize the fallout of a data failure by restoring from your backups.
Full management functions and ransomware protection with Tsukaeru Cloud Backup
With your computer and data backed up to the cloud on a regular basis, you never have to panic if a data failure suddenly occurs. Even if it is caused by a virus, malware, or a ransomware attack, your backup files are not affected at all, allowing you to keep your business up and running.
To learn more about the popular Tsukaeru Cloud Backup service from Tsukaeru.net and how it can help you safely and easily protect your data, please visit our website.
Click here for more information on Tsukaeru Cloud Backup.
.jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00
It is difficult to overstate the importance of backing up your computer or smartphone. All your data, your files, your contacts, your photos, etc. are a vital part of your digital life. This is especially true in the business world where this accumulated data is a valuable asset, making backups a must.
However, when it comes to backups, there are those who say, "It takes too long for the backup to finish, and it's a pain…" Indeed, if you have a massive number of files on your computer, it can take a considerable amount of time, sometimes as much as half a day.
In this article, we will take a look at using the cloud to backup your data and ways to make that process easier and faster.
Cloud backup in Japan
According to a survey conducted by the Japanese Ministry of Internal Affairs and Communications (MIC) in 2020, the percentage of companies using cloud services has been increasing year by year. That year it reached 68.7% breaking down to 39.4% for "company-wide use" and 29.3% for "use in some offices or departments." Data backup accounted for 36.5% of cloud service usage, a further increase from 31.4% in 2019.
Cloud backup advantages
One of the biggest advantages of cloud backup is the lower installation costs compared to large, in-house storage devices. This is especially true for small or medium-sized businesses that do not have large budgets. In addition to the cost, cloud backup does not require an in-house professional staff to perform daily maintenance.
Even if a great deal of money and manpower is used to set up your own backup, this does not necessarily guarantee efficiency and reliability. Technology is constantly changing, and it can be a struggle to stay up to date and secure from new threats. With cloud backup, on the other hand, you can rely on a professional company to monitor and maintain the latest backup infrastructure for you, thus ensuring high reliability and efficiency.
In addition, cloud backup is easily scalable. One major appeal is that you can choose the data capacity according to the scale of your business and then increase it as needed.
Cloud backup disadvantages
One disadvantage of cloud backup is that everything happens through the Internet, which can result in bandwidth problems during busy times. One solution is to set the backup schedule outside of business hours. For example, with Tsukaeru Cloud Backup provided by Tsukaeru.net, you can set the bandwidth to better manage speeds. However, no matter when you schedule the backup, as long as it is dependent on an Internet connection and depending on the amount of data, it may take some time to backup and restore.
Different backup types and how to increase data transfer speeds
What can you do if your backups are slow and time-consuming? Here are some tips to improve backup speeds that you can implement immediately.
External HDD backup
One of the most common backup methods is to save everything to an external hard drive (HDD). In this case, there are two main ways to improve the speed.
The first option is to use a USB 3.0 compatible cable for the data transfer. USB 3.0 is a new USB standard that improves transfer speeds up to three times more than the conventional USB 2.0. However, this method requires that the computer, cable, and external HDD are all USB 3.0. compatible.
The second option is to use specialized file transfer software (not the default function of the operating system) that can increase speeds and reduce backup times even for older computers that do not support USB 3.0.
.jpg)
Things to consider when choosing a cloud backup service
Due to the current global situation, more and more companies are turning to cloud backup. However, backup speeds depend largely on the cloud service used, making it very important to choose the right service. In order to choose a service with the best backup speeds based on your needs, we recommend that you compare the following points:
Cloud backup method
There are three main methods to protect your data using the cloud: full backup, differential backup, and incremental backup. Each of them will be explained in the next section below.
Server Location
Uploading time can vary depending on how far or close the server is to you and your data. Even though your information is digital, it still has to be transferred to a data center that physically exists. Therefore, backups with a cloud service using Japan-based servers will be faster for clients in the same country as compared to services with overseas servers.
Data recovery restrictions
Even if your cloud backup is fast, it is of little use if it requires a long time to restore your data. Some services enforce a certain limit on the download capacity or speed when restoring data, so make sure to fully understand any limitations when considering your options.
Cloud backup types (full, incremental, differential)
There are several cloud backup types to choose from, and with Tsukaeru Cloud Backup, you can select the most suitable format according to your needs.
With our default settings, the initial backup is a full backup with the second and subsequent backups being incremental backups. However, you can change the settings to "Always full," "Always incremental," or "Always differential."
Full backup
.jpg)
Just as it sounds, this is a complete backup of all the files on your computer. The first time you create a backup with Tsukaeru Cloud Backup, it will be a "full backup" and therefore will take the longest time.
Incremental backup
.jpg)
By default, Tsukaeru.net creates an incremental backup for the second and subsequent backups. This method detects and backs up only those files that have changed or have been newly created since the last backup, whether it was a full or incremental backup. This significantly reduces the backup time compared to a full backup.
Differential backup
.jpg)
While similar to an incremental backup, a differential backup copies all of the files, new and old, that had been added or changed since the last full backup. Because of the larger amount of data, a differential backup can take longer compared to an incremental backup.
With Tsukaeru Cloud Backup, you can also set the second and subsequent backups to be differential backups.
Tsukaeru Cloud Backup: Stress-free data protection
Backing up your data often requires time and effort, and it can quickly become an annoying chore. However, it is extremely important to protect your data on a daily basis. To ensure that this happens, it is recommended that you choose a backup method and service that is as stress-free as possible. With Tsukaeru Cloud Backup provided by Tsukaeru.net, you can easily back up your data to a dedicated server in Japan in as little as five minutes. Of course, this service provides incremental backups, which are superior in terms of speed. There are also no speed or capacity limitations when restoring. Please visit our website at the link below if you are interested in learning more about Tsukaeru Cloud Backup.
Click here for more information on Tsukaeru Cloud Backup.
(1).jpg)
Call toll-free: 0120-961-166
Office hours: 10:00-17:00


.jpg)
.jpg)
.png)
.jpg)
.jpg)

.png)
.jpg)
.jpg)

.jpg)
.jpg)
.jpg)
.jpg)
(2).jpg)
(1).jpeg)
(2).jpg)
.jpg)
.jpg)
.jpg)



.jpg)
.png)
.png)
.jpg)


.jpg)

.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
(1).jpg)
